Como verificar a identidade do usuário: Um guia para uma integração segura e sem problemas
Um blog sobre identidade do usuário, incluindo métodos de verificação populares, por que verificar a identidade do usuário é importante e o papel da verificação da identidade do usuário em relação à conformidade global.


Raul Liive
Como líder em fraudes e riscos, garantir que seu negócio permaneça à frente dos golpistas enquanto mantém uma experiência do cliente sem fricções é um desafio diário. Com um crescimento de 21% ano a ano em fraudes online (Relatório de Fraude da Veriff 2024) e o aumento de deepfakes, identidades sintéticas e engenharia social, você precisa de soluções que não apenas atendam às demandas regulatórias, mas também construam um forte caso para o apoio interno.
Para líderes como você—chefes de Fraude, Conformidade AML, Risco e Confiança & Segurança—verificação de identidade (IDV) é mais do que apenas uma caixa de verificação de conformidade. Trata-se de equilibrar segurança, experiência do usuário e impacto nos negócios, tudo enquanto assegura que as partes interessadas executivas vejam seu valor. Este guia divide as últimas tendências de fraude, estratégias eficazes de IDV e percepções chave para ajudá-lo a impulsionar o apoio interno para iniciativas de prevenção de fraudes.
O que é verificação de identidade do usuário e por que você deveria defendê-la?
O relatório recente da Comissão Federal de Comércio (FTC) revela que os consumidores relataram perdas de US$ 12,5 bilhões para fraudes em 2024, um aumento de 25% em relação ao ano anterior
Com as regulamentações se tornando mais rigorosas em todo o mundo e as ameaças cibernéticas se tornando mais sofisticadas, as organizações devem implantar soluções eficazes de IDV para proteger seus negócios, clientes e reputações. Se você tem um negócio online, garantir que seus clientes sejam quem afirmam ser não é apenas uma medida de segurança—é uma obrigação comercial. Desde a prevenção de fraudes até a garantia de conformidade regulatória, a verificação de identidade (IDV) é crítica para negócios que operam nos setores de serviços financeiros, jogos online, mobilidade e outras indústrias regulamentadas.
Verificação de identidade (IDV) é o processo de garantir que um indivíduo é quem afirma ser. Para equipes de fraudes e riscos, isso significa mitigar riscos financeiros e reputacionais, assegurar conformidade com PLD (Prevenção à Lavagem de Dinheiro), regulamentos KYC (Conheça Seu Cliente) e construir confiança interna em medidas de prevenção de fraudes.
Desafios comuns que a IDV resolve:
✔ Risco à sua reputação pessoal: Recomendar soluções de prevenção de fraudes ineficazes pode minar a confiança em sua expertise.
✔ Construindo um forte caso de negócios: Provando o impacto da IDV na prevenção de fraudes, conformidade e taxas de conversão.
✔ Convencendo as partes interessadas internas: Demonstrando ROI e eficiência operacional para os tomadores de decisão.
✔ Gerenciando a resistência das partes interessadas: Superando preocupações sobre a complexidade da implementação ou fricção com o cliente.
Métodos de Verificação de Identidade: Encontrando a combinação certa
Cada negócio tem riscos de fraude únicos, mas nem todos os métodos de IDV oferecem o mesmo nível de segurança e experiência do usuário. Veja como escolher a opção certa para sua organização:
1. Autenticação Biométrica
A autenticação biométrica verifica a identidade de um indivíduo com base em características biológicas únicas. É um método altamente seguro e amigável ao usuário que reduz a fricção enquanto garante alta precisão. As soluções de IDV biométrico podem reduzir as taxas de fraudes enquanto agilizam a inclusão—ajudando as equipes de prevenção de fraudes a construir um caso para adoção.
✔ Reconhecimento facial com detecção de vida garante que os golpistas não consigam usar fotos ou vídeos falsos.
✔ Tomada de decisão automatizada melhora a velocidade e reduz os custos de revisão manual.
✔ Líderes da indústria já estão adotando isto: Instituições financeiras, fintechs e plataformas online veem taxas de fraude reduzidas.
Com os ataques de deepfake aumentando em 300% em 2024, as empresas devem garantir que seus sistemas de autenticação biométrica incorporem detecção de vida para evitar tentativas de spoofing. Assista ao nosso vídeo com Chris Hooper e Geo Jolly para explorar biometria, IA e o futuro da prevenção contra fraudes:
A interseção entre IA e biometria está remodelando o futuro da verificação de identidade, trazendo tanto segurança aprimorada quanto novos desafios. A autenticação biométrica orientada por IA está se tornando um pilar fundamental nas estratégias de verificação de identidade, oferecendo autenticação de usuário contínua e altamente precisa. No entanto, o aumento da tecnologia deepfake e ataques sofisticados de spoofing tornou crítico para as empresas integrar a detecção avançada de vida e medidas de prevenção de fraudes orientadas por IA. À medida que os algoritmos de IA melhoram, os sistemas biométricos estão evoluindo para detectar anomalias, prevenir fraudes de identidade e garantir conformidade regulatória. As empresas que utilizam biometria aprimorada por IA podem reduzir significativamente a fricção de integração enquanto mantêm alta segurança, tornando essa tecnologia um componente crucial das soluções modernas de verificação de identidade.
2. Verificação de ID Online
Os sistemas de verificação online validam IDs emitidos pelo governo, comparando-os com selfies em tempo real ou capturas de vídeo. A plataforma de verificação impulsionada por IA da Veriff garante:
✔ Valida IDs emitidos pelo governo contra bancos de dados em tempo real.
✔ Melhora a conformidade com as leis de AML, KYC e verificação de idade.
✔ Minimiza a fricção com decisões de verificação instantâneas.
3. Autenticação de Dois Fatores (2FA)
A 2FA aumenta a segurança ao exigir um passo adicional de verificação, como uma senha temporária (OTP) enviada por SMS ou e-mail. Muitas instituições financeiras agora incorporam 2FA biométrico para proteção adicional.
✔ Adiciona uma camada extra de segurança além das senhas.
✔ Muitas empresas agora combinam autenticação biométrica com 2FA para uma prevenção de fraudes aprimorada.
Apenas a 2FA não é suficiente, mas combiná-la com IDV impulsionado por IA fornece uma robusta estratégia de prevenção de fraudes.
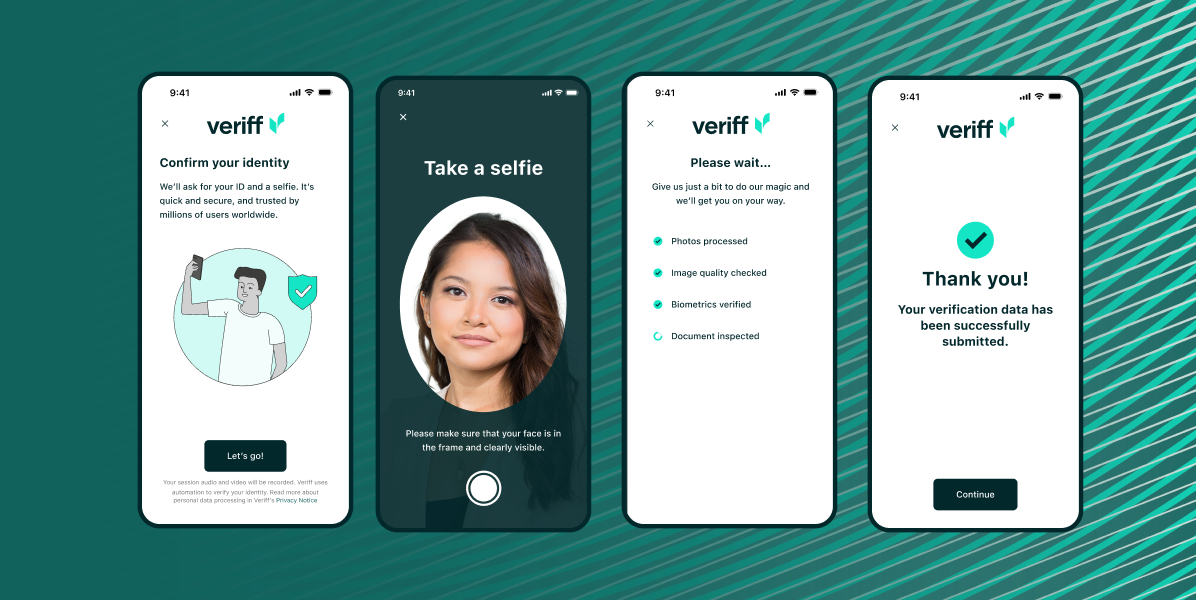
Como o processo de IDV funciona: Um guia passo a passo
✔ O usuário envia uma foto de seu documento de identidade. O sistema da Veriff identifica automaticamente o tipo de documento e verifica sua autenticidade.
✔ O usuário tira uma selfie ao vivo. A IA avançada garante que a selfie corresponda à foto do ID.
✔ A decisão de verificação é tomada. O sistema avalia o documento e os dados biométricos.
✔ O cliente é integrado. O usuário verificado tem acesso seguro aos serviços.
Com a verificação de identidade impulsionada por IA, as empresas podem reduzir os riscos de fraudes enquanto agilizam o processo de integração—ajudando a construir um ecossistema online mais seguro e confiável.
Como os serviços financeiros no Reino Unido estão fortalecendo a segurança com a Verificação de Identidade
Uma das indústrias mais críticas que requer verificação de identidade robusta é a de serviços financeiros, onde segurança e conformidade são primordiais. Em nosso estudo de caso de serviços financeiros do Reino Unido, exploramos como instituições líderes como Crown Agents Bank, Griffin, Finst, Fundvest e Monese implementaram com sucesso a verificação digital de identidade para aumentar a segurança, otimizar a integração de clientes e combater fraudes. Ao aproveitar a verificação orientada por IA, essas empresas melhoraram a confiança e a conformidade enquanto garantem uma experiência contínua para o usuário. O sucesso delas destaca a necessidade crescente de as empresas adotarem soluções avançadas de verificação de identidade para proteger os clientes e atender os requisitos regulatórios.
Ouça a conversa completa do Veriff Voice com Chris e Bonnie agora.
"O que realmente gostamos na tecnologia da Veriff é que ela mantém o usuário final dentro da jornada. Não permite que o indivíduo chegue até o final do processo e diga: "Desculpe, isso não funcionou". Em vez disso, orienta-os usando captura de imagem assistida ao longo do caminho. Segura sua mão – e é exatamente isso que, com nosso público, precisamos que ela faça."
IDV que funciona para seu negócio
Cada organização tem uma visão única de como equilibrar velocidade, conversão e mitigação de fraudes durante o processo de verificação de identidade. É por isso que a Veriff oferece as seguintes opções:
A Veriff oferece duas soluções de verificação de identidade (IDV) adaptadas às diferentes necessidades empresariais: Totalmente Automática e Híbrida. A solução Totalmente Automática é um sistema de verificação totalmente automatizado e orientado por IA projetado para empresas que priorizam velocidade, altas taxas de conversão e eficiência de custo. Ela oferece uma velocidade de verificação de 6 segundos, boa precisão e insights de risco aprimorados com a disponibilidade do RiskScore, tornando-a ideal para empresas que precisam de processos de verificação rápidos e contínuos. Por outro lado, a solução Híbrida combina tecnologia avançada de IA com especialistas em verificação, garantindo maior precisão, prevenção aprimorada de fraudes e segurança adicional por meio da supervisão humana. Esta opção é mais adequada para organizações que exigem um equilíbrio entre velocidade e segurança, proporcionando garantias de prevenção de fraudes e insights de risco. Ambas as soluções permitem que as empresas otimizem seus processos de IDV enquanto mitigam os riscos de fraude, aprimorando a confiança do cliente e a conformidade regulatória.
Considerações finais: O futuro da Verificação de Identidade
À medida que as táticas de fraude se tornam mais sofisticadas, as empresas enfrentam crescente pressão para se manter à frente com tecnologias de verificação de identidade (IDV) de ponta. O aumento de ameaças como deepfakes e fraudes de identidade sintéticas sublinha a urgência de autenticação biométrica em tempo real e monitoramento contínuo para detectar anomalias antes que se tornem questões sérias.
No entanto, abraçar soluções avançadas de IDV traz seus próprios desafios. As empresas correm o risco de danificar sua reputação pessoal se a decisão errada for tomada ao selecionar uma solução. Construir um forte caso de negócios para apoio interno e convencer partes interessadas chave, especialmente o Comprador Econômico, pode ser assustador. Além disso, gerenciar a resistência das partes interessadas a novas tecnologias muitas vezes se torna um obstáculo que atrasa o progresso.
As empresas devem priorizar plataformas de IDV avançadas e orientadas por IA como Veriff para proteger os clientes, garantir conformidade e construir confiança—tudo isso enquanto superam os desafios internos e oferecem uma jornada do usuário sem fricções. Com as apostas mais altas do que nunca, manter-se à frente na luta contra fraudes nunca foi tão crítico.


