Veriff Crypto Fraud Report: January to June 2020
We looked at the impact of financial crime and fraud on crypto in 2020, and the most prevalent types of fraud seen by Veriff, with data gathered from our verification flows.
Patrick Johnson
The cryptocurrency market is subjected to new law enforcements and the highest fraud rate compared to other industries that Veriff works with right now. In fact, this was still the case when we wrote our first fraud report, midway through last year, and this isn’t looking to change very fast.
The industry itself gains popularity day-by-day, by enabling faster and lower-cost international transactions, along with different promotional activities, which in turn lures criminals willing to cheat the system. And crypto itself is still seen in some quarters as a niche interest, but as the value of some of the more stable coins stays high, it’s worth understanding it all a little better.
To do that, we’d recommend our accompanying blogs - a Geek’s Guide to Crypto and Why Crypto is Ready for IDV to help you brush up before getting into the nitty gritty of this report.
As an illustration of the level of global financial crime within cryptocurrency alone, in 2019 cyber criminals were able to siphon away $4.26 billion from cryptocurrency users and exchanges. In the larger cases, this was down to sophisticated hacking of wallets address and exchanges, but like all financial crime, there are larger and smaller scale examples.
One of the more public examples of fraudulent activity around crypto took place on Twitter recently, as a number of celebrities had their accounts hacked, and links were placed with the enticement to “send money here and you’ll get double back”. Unsurprisingly, those who sent crypto saw none in return and the scammers were quickly taken down, but not before damage had been done.
We wanted to take a deeper look into the ways in which criminals look to exploit cryptocurrencies through identity-related fraud, the trends we’ve observed, and how Veriff is designed to help crypto fight back.
Veriff’s Fraud Prevention Tools
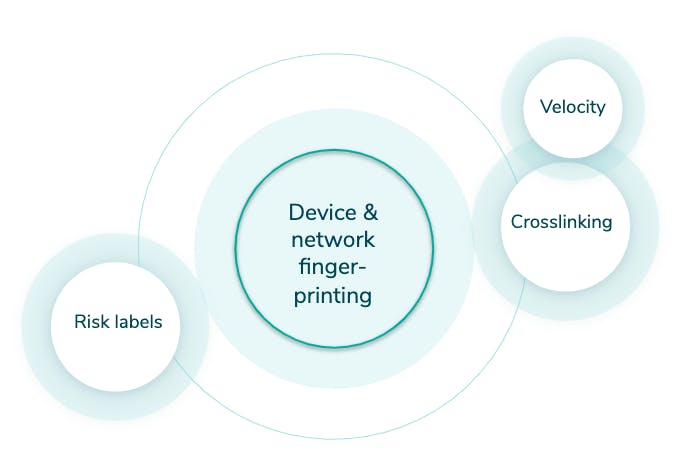
Veriff has an in-house built fraud prevention engine that is automating the decision making process and also assists specialists in case an automatic decision can’t be made (a hybrid approach). The engine can be broken into smaller pieces but all of them revolve around our proprietary device fingerprinting solution (see Graph 1).
Crosslinking
Crosslinking allows Veriff to group together sessions that share similar data points. Based on previous knowledge, fraudsters don’t tend to limit themselves to one try - they’ll try to get verified today, tomorrow and in the upcoming months and they won’t stop as long as they have fake identities. All the information from crosslinks is taken into account by our automatic decision engine, and is forwarded to our clients.
Graph 1. Veriff Fraud Prevention Engine
Velocity/Abuse
Velocity/Abuse ensures that no end-user abuses your service via multi-accounting. Taking into account all of the information we see through crosslinks, we can automatically shut down users if they, their document, or device have been approved before. We have three velocity checks that can be activated altogether or independently from each other:
- Duplicated user - checks whether the person has been approved before
- Duplicated document - checks whether the document has been approved before
- Duplicated device - checks whether the same device has been approved before
Risk labels
Risk labels point out the signs of fraudulent behavior in sessions. These labels are used by our specialists in more detailed security review and are forwarded to clients to give insight about the final decision and help in post analysis.
What types of fraud are we discussing here?
When it comes to Crypto, we can break fraud down into 4 main types:
- Document fraud
- Technical fraud
- Identity fraud
- Recurring fraud
We’ll look at each in depth, what they are, the types we see most regularly, and the impact within the crypto industry.
Document Fraud
This is often the type of identity fraud that leaps to mind first - tampered or entirely fake identity documents. These often exist in the form of fake IDs for a specific real world application - normally gaining access to something you’re underage for - but online there is normally more skill that goes into their creation, and they look to serve a monetary purpose, frequently some form of financial bonus on offer for inviting more users to a site.
So let’s look at both examples.
Tampered documents
There are various methods of tampering, but the end result always includes slight alterations made to a legitimate document in order to partially or entirely change the holder’s identity. Forgeries include but are not limited to:
- Altering or replacing the document image
- Overwriting document data with a pen, pencil or other simple tools
- Adding/removing specific document data or elements
Fake documents
While tampered documents are usually counterfeited original documents, fake documents include manipulations that try to imitate the appearance of a legitimate-looking document but in reality are reproductions of the original. Such forgeries might come in the form of:
- Alterations of government-issued document specimens that are publicly available
- Premade templates with inserted fake photos and document data
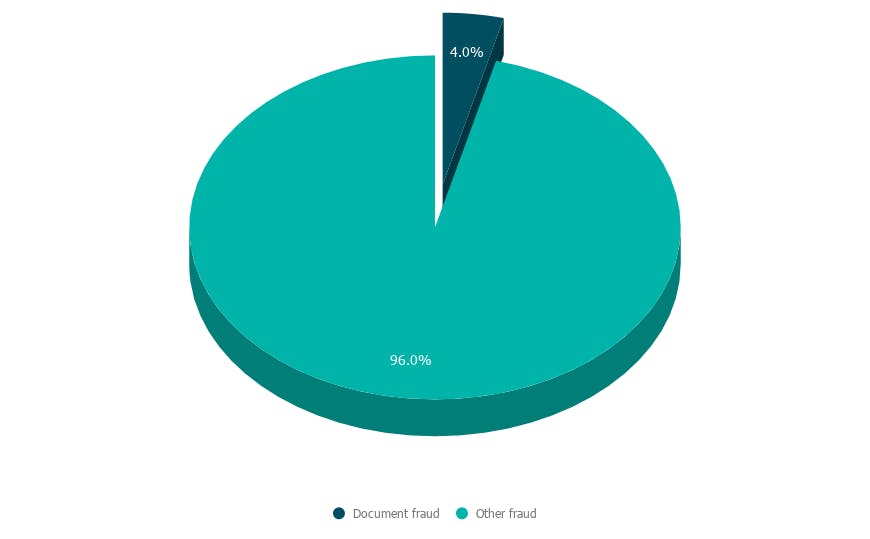
In the first 6 months of 2020, synthetic document fraud represented 4% of all fraud in the crypto market (see Graph 2)
Graph 2. Document fraud in crypto
How Veriff tackles document fraud
Our internal specimen database plays a key role in ensuring the accuracy of document fraud prevention. The database is updated on a daily basis as we carry out extensive document-related research (i.e. we find official specimens, information related to the issuing terms, etc) and cooperate with government authorities across the world.
In addition to our database, Veriff’s fraud prevention engine plays a crucial role in document fraud detection and prevention. When it comes to crypto, fraudsters usually tamper with documents in bulk. This means they often have various amounts of documents but also mobile devices to ensure some kind of anonymity. Luckily, with Veriff’s crosslinking we’re able to see data points that fraudsters are able to change.
Technical Fraud
This is exactly what you’d perhaps expect, fraud which involves a degree of technical skill that an average person wouldn’t possess. In this instance, we’re looking at streamed images and fraudulent access, two methods to take advantage of offers and make potential monetary gains.
Images and/or videos are streamed (or a slideshow)
This type of fraud happens when a verification includes media that’s coming from an emulated camera source. A fraudster might collect the portrait and document pictures belonging to different people in advance, edit them into a video and stream this inside Veriff’s flow to imitate the process being live.
Fraudulent access to the session
Whenever an end-user accesses the verification flow, we collect device and network information. Fraudulent accesses are defined as:
“Accesses associated with one verification session that has been accessed from different countries' networks and multiple devices.”
This is an indicator of the session link being fraudulently shared between different parties.
In the crypto realm, link-sharing cryptocurrency scams are initiated to get victims to sign up with legitimate documents, and then reap the benefits of an account takeover. Usually, a fraudster will create an account on a crypto site, entering all the victim’s information that has been scraped from the web, and when the time comes for verification, they send a link to the specific individual - saying ‘verification is required’ for some other purpose. This could range from getting a free box of chocolates, to some kind of exclusive discount, to anything really. We’ve seen a lot of examples!
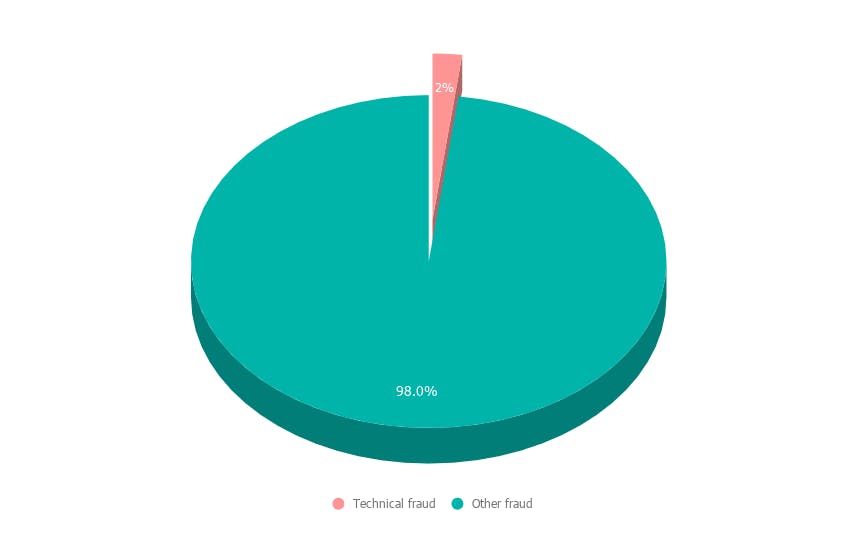
In the first 6 months of 2020, technical fraud represented 2% of all fraud in the crypto market (see Graph 3).
Graph 3. Technical fraud in crypto
How Veriff tackles technical fraud
Thanks to a comprehensive profile of device and network data, we have full control over exactly which pieces of information we use and in what context. We can utilize specific elements of device information, to spot whether camera emulation software was used at any point during the verification process.
We also perform checks on verification session images, and if there is little-to-no natural movement between them, we raise a risk label to flag this.
To prevent possible fraudulent access within sessions, we’ve developed a specific risk label that is triggered if we detect the session being accessed from different countries' networks.
Also added to the mix is crosslinking - if our fraud engine detects previous fraudulent accesses submitted by the same user, all their further verification attempts are automatically blocked as we consider it hard fraud.
Identity Fraud
Now we come to the two biggest types of fraud in the crypto market, the first of these being identity fraud. Not dissimilar to document fraud which we mentioned earlier, identity fraud is more about impersonation than actual document tampering. And that’s one of the two examples we’ll look to highlight - attempted impersonation and attempted deceit using fake images.
Attempted impersonation
Attempted impersonation is the intentional use of someone else’s identity document with the aim of obtaining access to the service on someone else’s behalf. This type of fraud usually uses an illegally obtained physical document of the victim presented by a fraudster.
Here’s a real life example from the Veriff team:
“Fraudsters put a fake job ad on a popular social media site claiming to represent a large company. Users applied for the job, and after that the scammers collected the applicants CVs and opened crypto accounts on their behalf. When identity verification for the crypto wallet was required, fraudsters sent verification links to ‘job applicants’ as part of a hiring process. Fortunately the “scammed people” contacted the company for whom they allegedly applied for a job and had done the verification for. Naturally they found out that online identity verification was not part of the company’s hiring process."
Image by Miina Vilo
Common impersonation scams:
Attempted deceit using fake images
The end-user doesn’t show a real physical document, but shows it from a device screen or a printed-out paper as they’re using someone else's digital document or a digitally manipulated document of their own.
In the first 6 months of 2020, identity fraud made up 34% of all fraud in the crypto market (see Graph 4).
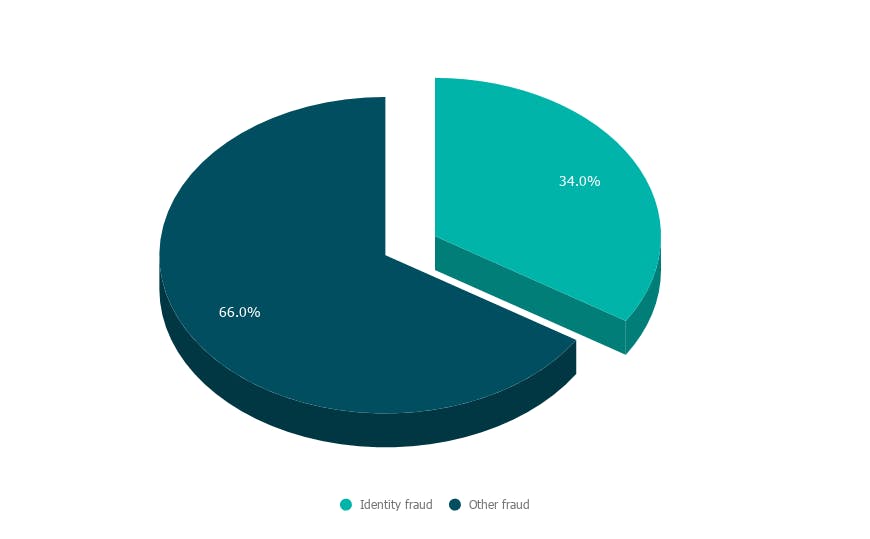
Graph 4. Identity fraud in crypto
How Veriff fights identity fraud
In order to detect whether a verification has been initiated with someone else’s physical document, we compare the faces from the selfie and document photo. If our confidence in the similarity is too low we decline the verification. If we’re not sure, we highlight the appropriate risks and leave the decision for a specialist.
If the same user tries to submit a different verification attempt in future, we can crosslink the incoming session with the previously declined sessions.
Recurring Fraud
Finally, we come to recurring fraud - and if you’ve been doing the addition through this report, you’ll know it makes up the lion’s share of fraud in the crypto market. This is also broken down into two examples, one of which is basic ‘recurring’ fraud, where a fraudster has been successful and come back to try again. The other is velocity abuse, which we’ll explain further below.
Here’s another story from the Veriff team:
“We noticed abnormal traffic associated with a car dealership located in the US. In addition to the store’s employees opening crypto accounts and verifying themselves at the spot in the shop, it seemed like shop’s customers were also asked to pose with their documents as a part of the ‘store procedure'. Some of the sessions were guided by what we think was an employee of the shop, some were carried out independently by customers sitting in cars. Unfortunately, this didn't lead anyone to getting a good discount at the car dealership, but a free crypto account was created on their behalf without their knowledge.”
Image by Miina Vilo
Recurring - Strong links to previous fraud
If fraudsters manage to abuse the system - they will come back and try again, if they fail to do so - they will come back and try twice as hard.
Velocity abuse - Investments chemes & scams
Cryptocurrency investments carry great opportunities but they experience the highest rates of multi-accounting due to different promotions involving free money. After getting approved once, fraudsters try to abuse the system and get approved as often as possible, which usually involves verifying different real users without telling them what they are being verified for. Fraudsters tend to go as far as creating synthetic identities, where they try to create a new identity by combining their real information in conjunction with fake data.
In the first 6 months of 2020, recurring fraud made up 60% of all fraud in the crypto market (see Graph 5).
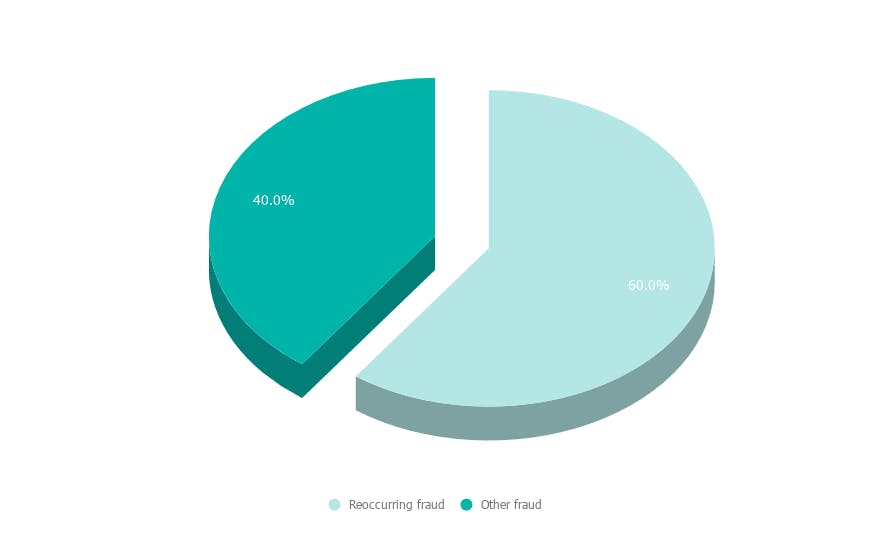
Graph 5. Recurring fraud in crypto
How Veriff fights recurring fraud
Recurring fraud is where crosslinks shine the brightest. If we’re confident that the end-user has committed fraud before, we’ll automatically decline all the recurring attempts associated with the same person, device or document.
If the same person, document or device have been found approved in the historically submitted sessions, all the recurring attempts will be declined with Velocity/Abuse.
The Overall Breakdown
Now that we’ve looked at the 4 different types of fraud that we’ve seen within the crypto industry, we can see the full breakdown below (see Graph 6):
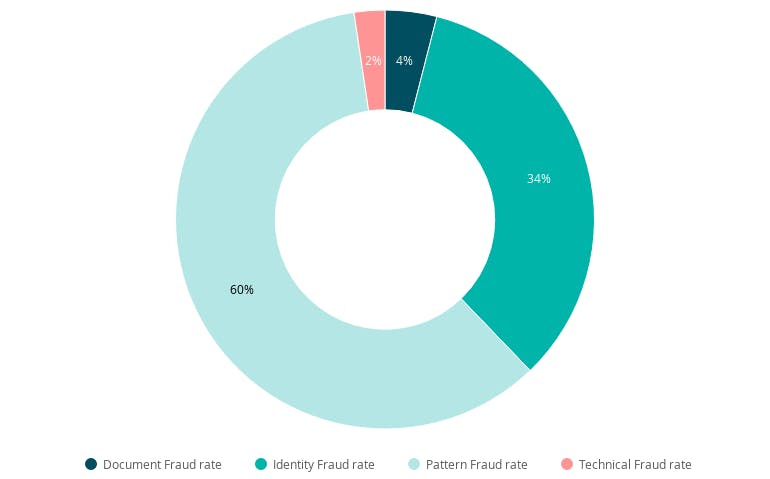
Graph 6. Fraud types in crypto
- Document fraud - 4%
- Technical fraud - 2%
- Identity fraud - 34%
- Recurring fraud/Pattern Fraud rate - 60%
Of course, in all of the above instances, Veriff is well-placed as a verification provider to fight against online fraud in all forms. We continue to observe trends across the crypto industry to stay ahead of developments and prevent losses for our crypto partners.




