O futuro da Gestão de Acesso à Identidade (IAM): Tendências e previsões para 2025
Aprofundamos na Gestão de Acesso à Identidade, como e por que isso afeta as empresas modernas, e as coisas cruciais que você precisa saber.


Raul Liive
Gestão de Acesso à Identidade é mais do que apenas uma solução tecnológica; é uma estrutura estratégica projetada para prevenir acesso não autorizado, proteger informações sensíveis e atender a requisitos regulatórios rigorosos
Para tomadores de decisão como CIOs, Diretores de TI e Chefes de Segurança, o IAM ajuda a garantir que o acesso à informação esteja alinhado com permissões específicas para cada função, reduzindo riscos associados a vazamentos de dados internos e externos.
As ferramentas de gestão de contas são projetadas para realizar três tarefas principais: identificar, autenticar e autorizar.
O IAM ajuda a prevenir acessos não autorizados a dados implementando permissões e papéis rigorosos para diferentes indivíduos dentro da empresa. Isso garante que apenas pessoal autorizado tenha acesso a informações específicas, reduzindo o risco de vazamentos de dados, tanto internos quanto externos.
Neste artigo, vamos explorar o assunto com profundidade, discutindo o papel da Gestão de Acesso à Identidade, os sistemas envolvidos e as tendências futuras associadas à integração dessas estruturas em sua empresa. A Gestão de Acesso à Identidade, ou IAM, é um aspecto crucial da estratégia de cibersegurança de qualquer empresa. Refere-se aos processos e tecnologias usados para gerenciar
Visão geral do mercado IAM
Em 2022, o mercado global de IAM foi avaliado em cerca de 16 bilhões de dólares americanos, com expectativas de crescer para mais de 43 bilhões de dólares americanos até 2029, principalmente devido aos seus benefícios em segurança dos funcionários e identificação de clientes. As políticas de IAM podem identificar proativamente comportamentos incomuns e detectar violações de políticas, enquanto automatizam direitos de acesso e atribuições de papéis. Ao examinar seus casos de uso, o IAM abrange vários componentes cruciais do mercado: Gestão de Acesso, Governança e Administração de Identidade (IGA), Gestão de Acesso Privilegiado (PAM), IAM da Internet das Coisas, bem como IAM do Cliente e tecnologias relacionadas.
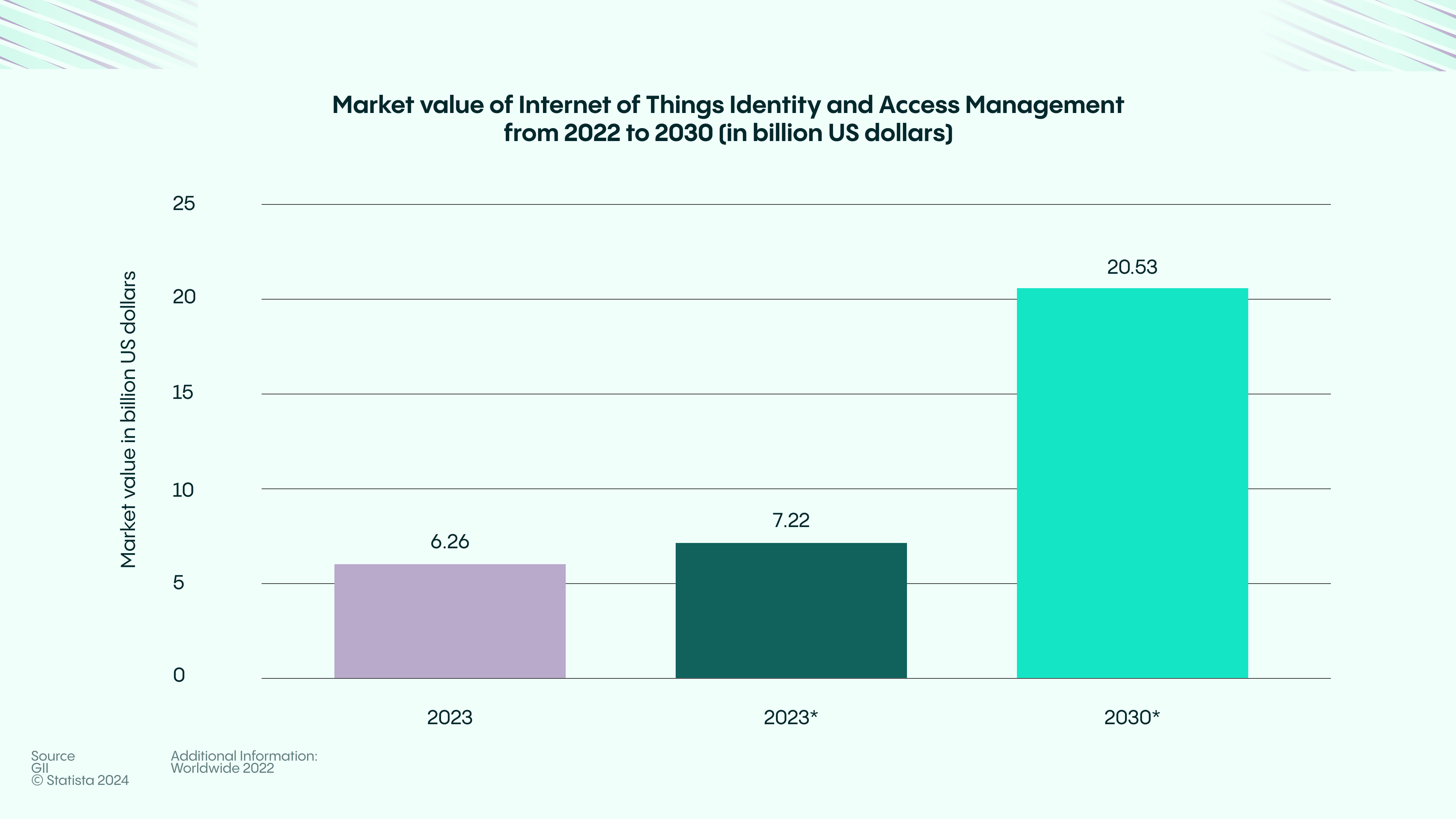
O gráfico mostra o crescimento projetado no valor de mercado global da Gestão de Identidade e Acesso (IAM) da Internet das Coisas (IoT) de 2022 a 2030. Em 2022, o mercado foi avaliado em aproximadamente 6,26 bilhões de dólares, e espera-se que cresça para 7,22 bilhões de dólares em 2023. Até 2030, o mercado deve alcançar 20,53 bilhões de dólares, destacando um crescimento significativo previsto. Essa tendência reflete a crescente demanda por soluções seguras de identidade e acesso, à medida que a adoção da IoT se expande globalmente, impulsionada pela necessidade de segurança em sistemas interconectados.
A Gestão de Acesso à Identidade (IAM) é altamente relevante tanto para os serviços financeiros quanto para os setores de mobilidade e transporte devido à sua dependência de controles de acesso seguros, conformidade regulatória e proteção de dados. Nos serviços financeiros, os sistemas de IAM ajudam a prevenir acessos não autorizados, proteger dados sensíveis de clientes e apoiar a conformidade com regulamentos rigorosos, como GDPR e CCPA. Ao implementar controles de acesso baseados em funções e autenticação multifatorial, as instituições financeiras reduzem os riscos de vazamentos de dados internos e externos e garantem eficiência operacional em ecossistemas financeiros complexos. No setor de mobilidade e transporte, o IAM é essencial para gerenciar identidades em uma variedade diversificada de usuários e dispositivos conectados, garantindo acesso seguro em ambientes impulsionados pela IoT e tecnologias conectadas. O IAM apoia interações seguras, previne o acesso não autorizado a sistemas críticos e se adapta a novos desafios de segurança, tornando-se um elemento fundamental para construir confiança e garantir segurança em redes de transporte.
Como o IAM funciona?
No início, os Sistemas de Gestão de Identidade eram compostos por diferentes partes básicas. Esses tradicionalmente envolviam vários métodos de autenticação para verificar uma identidade, como senhas, certificados digitais, etc. À medida que a tecnologia avançava, abordagens modernas começaram a se desenvolver, que incluíam elementos biométricos.
Devido ao ambiente tecnológico avançado e complexo, houve muitas mudanças consideráveis nos sistemas de IAM nos últimos anos - um nome de usuário e senha fortes não são mais eficazes. Os sistemas mais avançados de hoje incluem biometria, IA e Aprendizado de Máquina, e autenticação baseada em risco.
Benefícios principais do IAM para serviços financeiros e mobilidade/transporte
Controle de segurança aprimorado
Para CIOs e Gerentes de TI em serviços financeiros, o IAM oferece uma abordagem abrangente para evitar acessos não autorizados e proteger os dados dos clientes. O IAM permite que as empresas implementem controles de acesso baseados em funções, permitindo somente que indivíduos autorizados interajam com sistemas sensíveis, o que é essencial em setores que gerenciam grandes volumes de dados pessoais e financeiros.
Conformidade regulatória
Com regulamentações como LGPD, CCPA e requisitos específicos do setor, as empresas devem provar que gerenciam identidades de usuários e dados de forma responsável. Os sistemas de IAM não apenas apoiam a conformidade ao manter registros de acesso claros, mas também fornecem uma base para auditorias e proteção de dados, uma necessidade para o Gerente de TI ou Líder de Risco, que garante conformidade e gerencia riscos de segurança.
Eficiência operacional
Ao automatizar o processo de gestão de acesso, o IAM reduz a carga de trabalho das equipes de TI, minimizando também o risco de erro humano. Para o setor de TI, isso significa adotar um método eficiente para gerenciar permissões em uma diversidade de aplicações e sistemas, melhorando tanto a resiliência operacional quanto a segurança.
Aqui estão algumas tendências-chave do IAM em 2025:
Arquitetura Zero Trust
Primeiramente, a arquitetura de Zero Trust é esperada para se tornar mais proeminente. Nesse modelo, cada usuário ou dispositivo é tratado como uma potencial ameaça, garantindo a verificação contínua para acesso. A ideia central do modelo de segurança de zero trust é "nunca confie, sempre verifique," significando que usuários e dispositivos não devem ser automaticamente confiáveis, mesmo que estejam em uma rede segura.
Aprimoramentos em IA e Aprendizado de Máquina
IA e Aprendizado de Máquina (ML) estão preparados para melhorar os sistemas de IAM tomando decisões e previsões em tempo real para combater ameaças cibernéticas. Aqui, técnicas baseadas em IA como biometria comportamental, análises preditivas e respostas automáticas desempenharão um papel crucial.
Identidade descentralizada com Blockchain
A identidade descentralizada, impulsionada pelo Blockchain, é outra tendência antecipada. Esse conceito dá aos usuários controle sobre seus dados de identidade, melhora a privacidade e a segurança e reduz o risco de violações centralizadas.
IAM para IoT e Computação na Borda
Além disso, à medida que a IoT e a computação na borda se expandem, os sistemas de IAM se adaptarão para gerenciar identidades em uma multitude de dispositivos conectados
Autenticação sem Senha
Por fim, métodos de autenticação sem senha como biometria e tokens de hardware se tornarão padrão até 2025, oferecendo melhor segurança e experiência do usuário.
Como a Veriff pode ajudar a resolver os desafios do IAM para serviços financeiros e mobilidade/transporte
No setor de serviços financeiros e mobilidade e transporte, a Veriff está comprometida em criar ambientes digitais mais seguros através de nossas soluções de identidade inovadoras. Nossos serviços ajudam empresas a estabelecer confiança, simplificar operações e aumentar a segurança via integração de ferramentas abrangentes de Gestão de Acesso à Identidade (IAM).
A Veriff oferece um conjunto de capacidades adaptadas às necessidades únicas desses setores, incluindo verificação de identidade, prevenção de fraudes e aprimoramentos de IAM orientados por conformidade. Aqui está como a Veriff fortalece as soluções de IAM para os serviços financeiros e indústrias de mobilidade e transporte:
Verificação de identidade
A Veriff fornece a verificação de identidade em tempo real, garantindo que apenas usuários autorizados tenham acesso a sistemas e dados sensíveis. Verificando a identidade de um usuário por meio de verificações de documentos, verificação biométrica e detecção de vida, a Veriff adiciona uma camada segura ao processo de IAM, especialmente útil para indústrias com requisitos de conformidade rigorosos.
Autenticação biométrica
Com soluções biométricas avançadas, a Veriff ajuda a garantir que a pessoa acessando um sistema corresponda à identidade cadastrada. Isso é essencial para sistemas de IAM que dependem da autenticação multifatorial (MFA), adicionando uma camada adicional de segurança ao verificar usuários por meio de características físicas únicas.
Prevenção de fraudes
As capacidades de prevenção de fraude da Veriff ajudam as organizações a detectar e bloquear tentativas de acesso fraudulento em tempo real. A plataforma usa aprendizado de máquina para detectar anomalias e sinalizar atividades de alto risco, apoiando a gestão segura de acessos e minimizando acessos não autorizados.
Onboarding automatizado
Os serviços de integração da Veriff simplificam a integração de usuários ao automatizar verificações de identidade, verificação de documentos e outros processos de autenticação. Isso ajuda as organizações a ampliar seus esforços de IAM, gerenciando eficientemente o acesso para novos usuários enquanto mantêm padrões de conformidade e segurança.
Conformidade de dados e suporte regulatório
As soluções da Veriff estão em conformidade com o GDPR, CCPA e outras normas regulatórias, oferecendo tranquilidade para indústrias onde a proteção de dados é fundamental. Esses recursos de conformidade garantem que o suporte IAM da Veriff esteja alinhado com leis de privacidade de dados globais e regionais.
Fluxo de verificação personalizável
A Veriff permite que organizações personalizem fluxos de verificação de acordo com suas políticas de IAM, permitindo diferentes níveis de verificação com base em perfis de risco dos usuários ou necessidades de acesso. Essa flexibilidade ajuda as empresas a personalizar os protocolos de IAM de acordo com suas estruturas de segurança.
Esses serviços ajudam a fortalecer os sistemas de IAM, garantindo que apenas usuários legítimos tenham acesso a dados críticos, apoiando as organizações na manutenção de controle de acesso seguro, em conformidade e eficiente.
Perguntas frequentes
1. O que é o modelo Zero Trust em IAM?
O modelo Zero Trust é uma abordagem de segurança que requer verificação contínua de usuários e dispositivos, assumindo que nenhuma entidade é confiável por padrão, seja dentro ou fora da rede.
2. Como a IA impactará os sistemas IAM?
A IA aprimorará os sistemas de IAM ao habilitar tomada de decisão em tempo real, autenticação adaptativa e detecção automatizada de ameaças, fortalecendo a segurança no final.
3. O que é identidade descentralizada?
Identidade descentralizada permite que usuários controlem seus dados de identidade, em vez de depender de autoridades centralizadas. A tecnologia blockchain deve desempenhar um papel significativo nessa mudança.
4. Por que a autenticação sem senha é importante para o futuro do IAM?
A autenticação sem senha reduz o risco de ataques baseados em credenciais e melhora a experiência do usuário ao eliminar a necessidade de senhas, tornando-se um elemento crucial das futuras soluções de IAM.
Explore mais
Fique por dentro das notícias da Veriff. Assine o nosso boletim informativo.
Veriff só usará as suas informações para compartilhar atualizações do blog.
Você pode cancelar sua inscrição a qualquer momento. Leia nossos termos de privacidade



