Demystifying Intrusion: What is Account Takeover Fraud?
Account takeover fraud can cause a great number of problems for businesses and customers alike. However, it can also be incredibly difficult to detect and prevent. This is because many of the actions that criminals take are identical to the actions that are taken by customers and clients on a daily basis.

Chris Hooper
Account takeover fraud (ATO) occurs when a fraudster or criminal gains access to a customer’s account.
Once the fraudster has accessed an account using stolen data, they can then make a series of unauthorized changes. This includes taking steps such as altering the personally identifiable information associated with the account, or changing the usernames passwords. When this step is complete the criminal will then carry out numerous unauthorized transactions.
Once ATO fraud has occurred, it can be difficult for the customer to reclaim the account without suffering a financial loss. The relationship between the customer and the business involved may also be irrevocably damaged.
Any kind of online account can be taken over by a criminal actor, but popular examples include bank accounts, credit cards, government benefits accounts, store loyalty cards, savings accounts, and email accounts.
Methods used in account takeover - how criminals get confidential information
In order to gain access to an account, most fraudsters buy stolen credentials on the dark web. As soon as the fraudster has purchased this information (which is usually verified in advance), they can access a customer’s account and make the changes required to make purchases.
Most of the information available for sale on the dark web comes from data breaches. The Identity Theft Resource Center (ITRC) reports that just over 285 million individuals were impacted by publicly reported data breaches in 2021 alone. Experts predict that this number will continue to climb as attackers use more sophisticated methods to target websites.
However, purchasing stolen data is just one way that criminals can obtain personally identifiable information. On top of this, fraudsters may also use malware, phishing or other methods of identity theft to obtain customer login and password information.
Similarly, if a hacker obtained a customer’s credentials, they may then employ a technique known as credential stuffing. Using this tactic, the hacker will try to use the user’s login and password information from one site on their other accounts. If the victim often reuses passwords, they’ll be successful.
On top of all these methods, a criminal actor may try to execute a brute force attack. As part of this technique, a hacker will use bots to try multiple passwords on a single website. Other ways a criminal may attempt to commit account takeover fraud include man-in-the-middle (MitM) attacks, call center fraud, and SIM swapping.
How hacked account information could be used
When a criminal gains access to an account, they can use it to make purchases, order new cards, or claim benefits.
The exact way hacked information can be used varies based on the type of account a criminal accesses. For example, if a criminal accesses a loyalty rewards account, they may spend the account credits or rewards points for their own benefit. Alternatively, if they access a bank account, they make a payment to a fraudulent company or order a new debit card to their address.
Other ways hacked information may be used by a fraudster include:
- Ordering a new card from the user’s credit card company and using this card to make fraudulent purchases
- Purchasing a new smartphone from a user’s mobile phone carrier
- Opening a new bank account in the victim’s name
- Accessing and stealing other pieces of personally identifiable information
- Using stolen information to access other accounts
- Changing the account information (such as the associated phone number, email address, and home address associated with the account)
- Selling the verified account information on the dark web
- Redirecting any benefits received
- Man-in-the-middle attacks - In cryptography and computer security, a man-in-the-middle attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties.
How to protect clients from account takeover fraud
Account takeover fraud can cause a great number of problems for businesses and customers alike. However, it can also be incredibly difficult to detect and prevent. This is because many of the actions that criminals take are identical to the actions that are taken by customers and clients on a daily basis.
For example, a criminal will often change account preferences once they’ve gained access to the account. This is so that the victim doesn’t receive any notifications that may indicate their account has been compromised. However, this action is indistinguishable from a customer or client simply changing their preferences because they’re receiving too many notifications.
Similarly, when a hacker changes the details associated with a customer’s account, it can be difficult for a business to tell whether or not this is actually the customer. For example, a customer may simply be changing the associated delivery address because they’ve moved home.
That said, there are steps businesses can take to protect their clients from account takeover fraud.
Educate clients on the importance of account safety
One of the easiest ways of preventing account takeover fraud is to educate your clients on the importance of keeping data safe. If you can change client behavior, you can make accounts harder to access. So, remind your clients to:
- Stop reusing passwords
- Update their passwords regularly
- Use a password manager
- Access sites directly rather than using email links
- Check URLs for errors and misspellings
Improve your communication
As well as making sure that your clients know how they can safeguard their accounts, you should also make sure that you openly communicate with them about account changes. This way, if a fraudster accesses their account, you stand the best chance of stopping the takeover as quickly as possible.
For example, if a client changes their contact information or the address that’s registered to their account or in social media, then you should send them an email acknowledging the change as soon as it takes place. Within the email, you should provide the client with contact information for your customer services team. This way, they can get in touch with you immediately if they didn’t make the requested change.
Upgrade your security systems
On top of this, you should also improve your security systems and ensure that data protection practices are followed at all times. Steps you can take include:
- Using SSL on pages that collect personally identifiable information
- Using encryption
- Limiting user input to ensure your site code is not vulnerable to SQL or HTML injection attacks
- Ensuring that your security system is not reliant on static passwords and instead uses a multi-factor authentication solution that includes biometrics
Account takeover resources
To help your business prevent account takeover fraud from taking place, we’ve put together a fantastic range of resources. Take a look below to discover more about how you can detect fraud, prevent it from taking place, and recover accounts.
Account takeover fraud statistics
The latest account takeover fraud statistics show us exactly how prevalent this type of fraud is.
In this guide, you can learn exactly how quickly the rate of online fraudulent attacks is growing, whether account takeovers are on the rise, and how many American citizens have been victims of account takeovers. It will show you just how big the problem is and exactly why your business must proactively safeguard client accounts.
Types of account takeover fraud
Today, the techniques used by fraudsters when attempting to take over an account are becoming increasingly complex. In this extensive guide, we detail six major types of account takeover fraud. We also highlight the security measures your business can put in place to stop these attacks from occurring.
Detecting account takeover fraud
One of the best ways of maintaining the client-business relationship is by detecting account takeover fraud early. In this guide, we explain the fraud detections you can put in place, as well as other ways that your business can detect and stop account takeover attacks. We also examine some of the ways you can prevent account takeover fraud in the first place, and how you can enlighten your customers about the steps they can take to secure their accounts.
Prevent account takeover fraud
Interested in discovering more about how your business can prevent account takeover fraud from taking place? Well, this is the guide for you. Here, we discuss how account takeovers happen, what happens during an account takeover, and how your business can detect that an account takeover attack is taking place.
Account takeover fraud recovery
Account takeover fraud carries a number of financial and reputational risks. If account takeover fraud occurs, then it’s vital that your business recovers and secures these accounts as quickly as possible. In our guide to account takeover fraud recovery, we provide an overview of what account recovery includes and the steps you can take to recover from an account takeover.
See how Veriff’s fraud detection solutions can help you - Book a demo
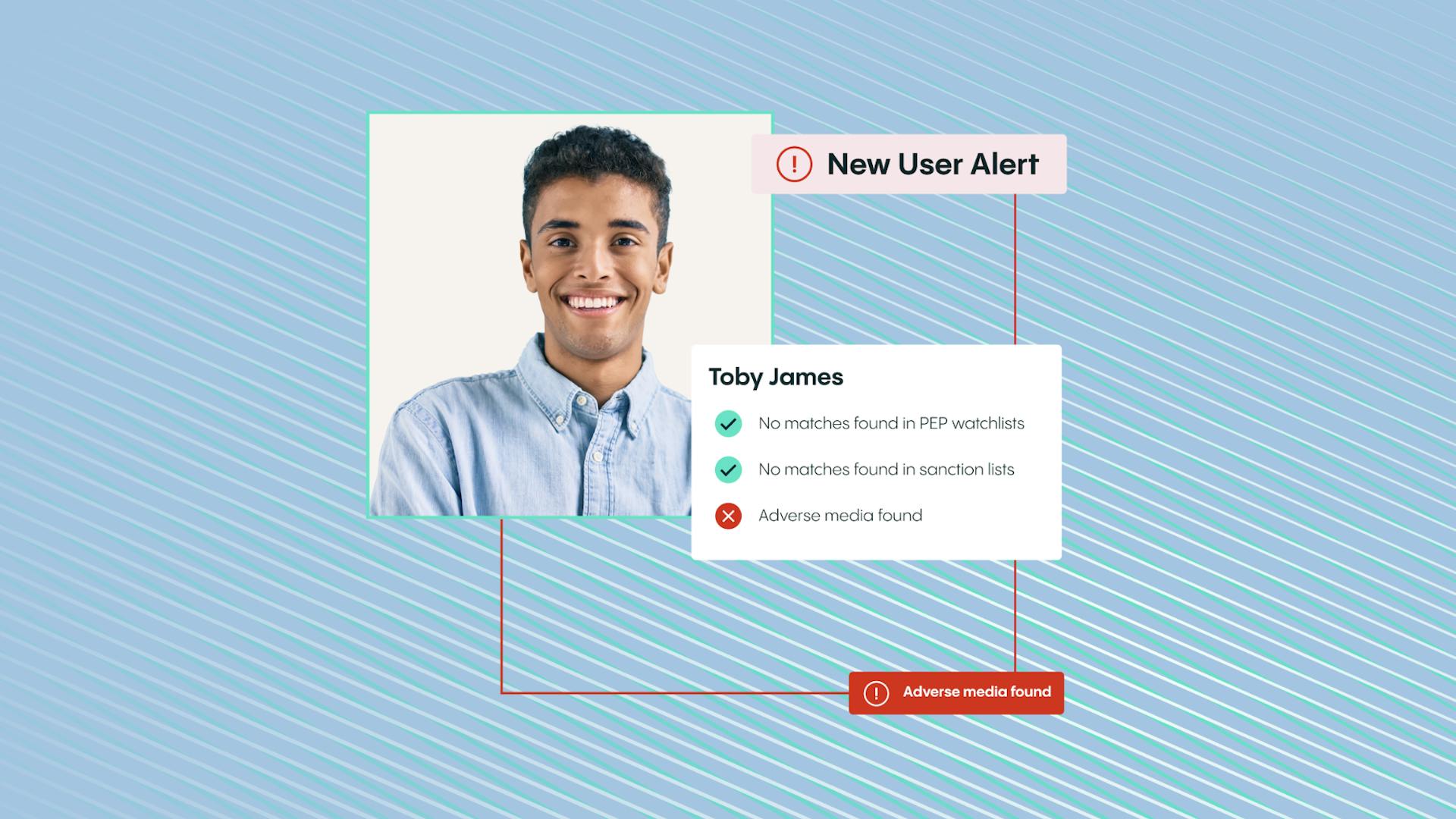
To prevent account takeover fraud from taking place, your business must employ the correct fraud detection processes. With the help of these processes and systems, you can stop fraudsters before they can access customer accounts.
Here at Veriff, we offer a range of real time fraud detection solutions that can help you secure customer accounts. For example, both our identity verification solution and our AML screening solution can help you verify new users before you onboard them. Plus, our biometric authentication solution can be used to match returning users and detect account takeover fraud.
If you’re interested in learning more about how our fraud detection solutions can help your business, talk to our fraud prevention experts today. We’d love to provide you with a personalized demo that shows exactly how our solutions can help keep your business and customers safe.


