Como a Veriff mantém seus dados seguros
Veriff está na posição privilegiada de lidar com vastas quantidades de dados privados e pessoais de indivíduos todos os dias. Isso não é algo que levamos na brincadeira, e como a confiança é o nosso negócio, queremos ser transparentes sobre nossas práticas de segurança em como mantemos suas informações pessoais seguras em todos os momentos.


Aleksander Tsuiman
Verificar se um indivíduo é quem diz ser no mundo virtual é uma prioridade para muitas empresas. Tornar a Internet um lugar mais seguro para todos é também a razão principal pela qual a Veriff foi fundada. Para alcançar isso, devemos prevenir fraudes de identidade reduzindo a anonimidade e promovendo uma maior confiança em todas as interações online. No entanto, a fraude é comum no mundo online de hoje. Por exemplo, um relatório da Juniper Research de 2023 estimou que as perdas com fraudes em pagamentos online devem ultrapassar US$362 bilhões globalmente nos próximos 5 anos. Segundo a Federal Trade Commission (FTC), os relatos de roubo de identidade dobraram em 2020 em comparação a 2019, destacando o risco aumentado no espaço digital. O roubo de identidade relacionado a cartões de crédito lidera a lista dos tipos de roubo de identidade relatados em 2023. A FTC recebeu 416.582 relatos de indivíduos que disseram que suas informações foram usadas indevidamente com um cartão de crédito existente ou ao solicitar um novo cartão de crédito.
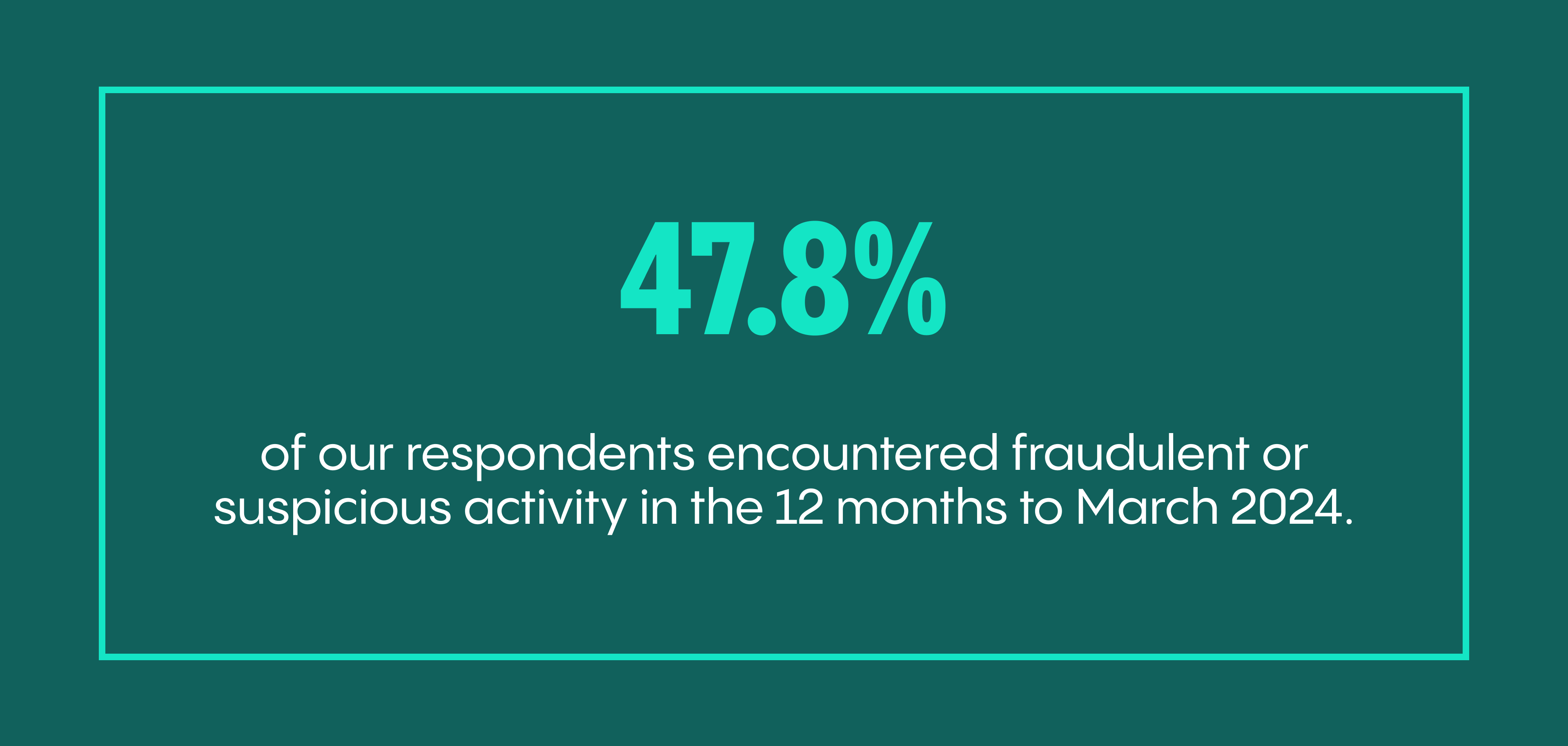
A Veriff também publicou continuamente seus próprios relatórios de fraude.O Índice de Fraude da Veriff 2024 e sua pesquisa acompanhante destacam que 47,8% dos entrevistados encontraram atividade fraudulenta ou suspeita nos últimos 12 meses até março de 2024
Veriff está comprometida em construir confiança online, por isso é especialmente crucial que os indivíduos possam confiar em uma empresa de verificação de identidade como a Veriff com seus dados.
No entanto, compartilhar seus dados pessoais, como seu documento de identificação, online pode levantar algumas dúvidas. A verificação de identidade deve ser um caminho para um espaço online mais seguro e não uma barreira, por isso é essencial que o processo de verificação online seja simples e transparente. Além disso, é trabalho da Veriff garantir a conformidade com os requisitos de segurança e proteção de dados. Para adicionar mais transparência, neste blog, descreveremos algumas das maneiras como garantimos que seus dados estejam sempre seguros
A Veriff é dedicada à sua conformidade com o mais alto padrão das leis de privacidade e proteção de dados, como o Regulamento Geral de Proteção de Dados (GDPR) da União Europeia. A conformidade com as leis é sempre respaldada pela prioridade central da Veriff - que é garantir a segurança de seu serviço. No coração da conformidade da Veriff estão medidas organizacionais e técnicas que garantem um processamento seguro dos dados. Aqui estão alguns exemplos de elementos-chave a entender sobre o processamento de dados pessoais e as melhores práticas seguidas pela Veriff.
1. Processamento de dados pessoais
Seus direitos. A Veriff reconhece cada indivíduo que passa pelo seu fluxo de verificação como um sujeito de dados. O sujeito de dados está sempre no centro do serviço da Veriff. Você, como sujeito de dados, tem direito a informações específicas e a exercer seus direitos de privacidade de dados. É por isso que a Veriff deixa claro em seu Aviso de Privacidade que a Veriff está fornecendo seus serviços de verificação a outras empresas - a Veriff coleta seus dados via seu serviço de verificação apenas se você foi direcionado para lá por um cliente comercial da Veriff. O cliente da Veriff, a empresa que pede que você verifique sua identidade, é quem decide como e para quais propósitos a Veriff processa seus dados. Isso também significa que eles devem informar a você como eles e a Veriff processam seus dados e garantir que você possa exercer seus direitos ao longo do caminho.
Os serviços da Veriff processam dados pessoais. O Regulamento Geral sobre a Proteção de Dados da UE (conhecido como GDPR) define dados pessoais como qualquer informação sobre um indivíduo que pode ser identificado, direta ou indiretamente, por nome, número de identificação ou outros fatores relacionados à identidade física, fisiológica, genética, mental, econômica, cultural ou social de um indivíduo. Os dados coletados pela Veriff para sua identificação são dados pessoais e os clientes da Veriff devem garantir que possuem uma base legal válida para permitir que a Veriff utilize os dados para seus serviços.

Os serviços da Veriff podem processar dados pessoais sensíveis. Dados sensíveis são uma subcategoria de dados pessoais. Existem diferentes definições de 'dados sensíveis' em diferentes países. No entanto, geralmente se centra em dados que revelam origem racial ou étnica, opiniões políticas, crenças religiosas ou filosóficas, filiação a sindicatos, e dados genéticos, dados biométricos (para o propósito de identificar uma pessoa de forma única), dados de saúde, ou dados relacionados à vida sexual ou orientação sexual de uma pessoa. Como parte de seu serviço, a Veriff pode processar seus dados sensíveis. Por exemplo, os serviços da Veriff podem processar informações sobre seu rosto, o que equivale a dados biométricos. Esta é uma observação importante, pois dependendo de por que nossos clientes estão usando nossos serviços, eles podem precisar seguir requisitos legais mais rigorosos. Embora os requisitos em torno do processamento de biometria sejam rigorosos, é importante notar que a biometria pode fornecer uma forte camada de segurança contra atores maliciosos enquanto também minimiza a quantidade de dados processados.
Supervisão por autoridades. A conformidade com as leis de privacidade de dados no mundo todo está sob maior escrutínio das autoridades locais de proteção de dados. A Veriff também é supervisionada por autoridades locais de proteção de dados e garante total cooperação com as autoridades de diferentes Estados-Membros da UE e além.
2. Avaliações de risco e uma equipe dedicada
A equipe dedicada de privacidade e conformidade da Veriff, junto com nosso responsável pela proteção de dados, realiza consistentemente avaliações de impacto sobre a proteção de dados. Essas avaliações de impacto não apenas atendem aos requisitos legais, mas também permitem que a Veriff identifique e aborde proativamente os riscos relacionados aos nossos produtos e serviços. Ao aproveitar nossa competência jurídica interna e tomar medidas proativas, a Veriff garante o mais alto nível de segurança de dados para manter nosso compromisso em proteger sua privacidade.
3. Proibição de venda ou compartilhamento não autorizado de dados do usuário final
Conforme declarado no Aviso de Privacidade da Veriff, divulgaremos seus dados pessoais ao cliente que nos autorizou a fornecer o serviço de verificação de identidade. Além disso, como parte integrante do serviço de verificação de identidade, seus dados pessoais podem ser divulgados a nossos subprocessadores cuidadosamente selecionados. Estes são prestadores de serviços que nos ajudam com diferentes serviços de processamento e armazenamento de dados, sendo essenciais para proporcionar nosso serviço de verificação de identidade. Internamente, qualquer acesso a dados é concedido com base na necessidade e no princípio do menor privilégio. Isso significa que nossos funcionários têm acesso apenas às informações e direitos necessários para suas tarefas específicas. Isso garante que seus dados estejam sempre seguros, sem acesso não autorizado
4. Períodos fixos de armazenamento de dados
O prazo para manter seus dados está fixado em políticas internas e acordos com clientes. A Veriff nunca mantém dados indefinidamente. Por exemplo, como padrão, dados pessoais que são processados em nome de nossos clientes são armazenados por no máximo 3 anos. No entanto, no contexto dos serviços de verificação de identidade, isso pode diferir dependendo das instruções do cliente. É por isso que a empresa que solicitou sua verificação de identidade é a que pode informar exatamente por quanto tempo seus dados são armazenados e usados para verificação de identidade.
5. Criptografia em repouso e em trânsito
Na Veriff, os dados são criptografados tanto em repouso quanto em trânsito. A criptografia é o processo de converter dados em um formato ilegível, tornando-os inacessíveis ao usuário que não possui a chave de descriptografia. A criptografia possibilita a proteção segura e confidencial dos dados de ponta a ponta, protegendo seu conteúdo.
Os dados em trânsito são criptografados usando o Transport Layer Security (TLS) 1.2 ou versão mais nova. O TLS é o protocolo que permite que dispositivos digitais (como computadores e telefones) se comuniquem de forma segura pela internet, sem que a transmissão fique vulnerável a um público externo. Os dados em repouso são criptografados usando o padrão de criptografia avançada AES-256. O AES é um cifrado de chave simétrica, o que significa que a mesma chave é usada tanto para a criptografia quanto para a descriptografia dos dados.
Além disso, todos os aplicativos internos hospedados pela Veriff e usados para gerenciar dados pessoais também são redirecionados para VPN como uma medida extra para reduzir a superfície de ataque e fornecer uma camada adicional de proteção em torno do TLS padrão.
6. Segurança por design e por padrão
A Veriff adquiriu e manteve por anos a certificação SOC 2 Tipo 2 de conformidade. Isso confirma que os sistemas da Veriff são projetados para manter os dados de seus clientes seguros. Quando se trata de trabalhar com um provedor de serviços de verificação de identidade, tal confiabilidade é absolutamente crucial, pois estamos bem cientes de que casos de vazamentos de dados pessoais podem ter consequências que mudam a vida.
A Veriff também recebeu certificação contra o padrão ISO/IEC 27001:2022, um padrão internacionalmente reconhecido de segurança da informação publicado pela Organização Internacional de Normalização (ISO). A Veriff também está certificada contra o esquema Cyber Essentials do Reino Unido, que foi projetado para ajudar a proteger organizações contra uma variedade de ataques cibernéticos mais comuns. Você pode aprender mais sobre os Cyber Essentials na página do Centro Nacional de Segurança Cibernética do Reino Unido.
Essas medidas de segurança são apenas alguns exemplos que são implementados aqui na Veriff. Temos todas as precauções necessárias para lhe proporcionar tranquilidade ao usar nosso serviço de verificação de identidade. Estamos sempre acompanhando as atualizações relevantes e implementando medidas adicionais para garantir conformidade.
7. Onde você pode ler mais?
Estamos sempre animados para ouvir seu feedback, opiniões e ideias - você pode encontrar maneiras de nos contatar em nosso Aviso de Privacidade.
Você pode aprender mais sobre nossas práticas de segurança na página Segurança e Conformidade e no Centro de Confiança da Veriff.


