What is Biometric Authentication and Verification?
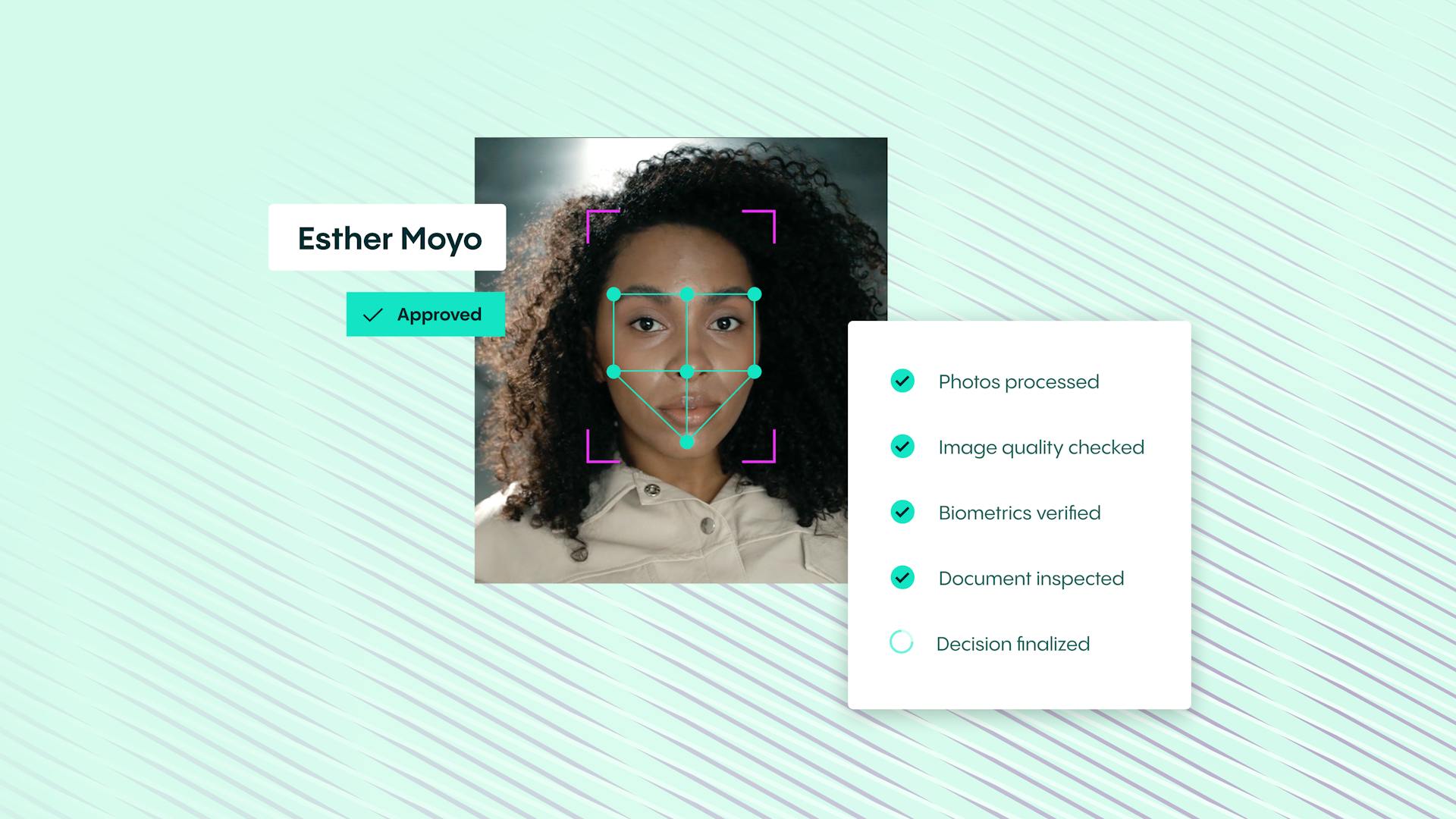
Biometric authentication is the process of comparing a user's live identity to the biometrics you already have. Biometric verification, on the other hand, is when you validate a user's official ID documents.
Ucha Vekua
Put simply, biometric authentication is a procedure that verifies an individual based on their unique biological characteristics. It helps you to verify people and make sure that they are who they claim to be in a matter of seconds. The way it works is pretty simple - a database stores authentic data, which you can then compare with your user's physical traits. Generally, you can use biometric authentication technology to help users reset their credentials, deal with high-risk customers, or verify your remote employees.
Think of the Face ID technology in smartphones or an electronic fingerprint recognition system, also known as Touch ID. These are both clear and probably the most popular examples of biometrics. They are using a person's unique physical characteristics to make a momentary verification happen. Biometric authentication is increasingly becoming common in various security systems and point of sale (POS) applications.
Let's dive deep into this topic. We'll tell you all about the advantages of using these systems and show you some examples of companies doing so.
What is the difference between authentication and verification?
Even though both authentication and verification are methods to identify if the users are who they claim to be, they are slightly different terms.
Authentication is the process of comparing a user's live identity to the biometrics you already have. Verification, on the other hand, is when you validate a user's official ID documents.
Usually, the verification procedure happens only once - a person just needs to validate their official ID Document before starting to use a particular service. But they still need to authenticate themselves each time they want to access it. From the user's perspective, the main difference between identification and authentication is the UX (user experience) - verification requires your ID data, and authentication requires information about your biometrics.
Also, time is an important factor that differentiates the authentication and verification procedures. Authentication happens instantly because the system needs to make a comparison with the data it already has. But verification might take a little longer as it needs to validate your identity and make sure that it passes all the security checks. Companies use both of these services accordingly to ensure that their systems are secure and build trust over the internet.
Biometric authentication examples
Biometric authentication is a very useful solution for several services online. Because of its efficient and secure procedure, authentication is the first choice for many companies to use as a security feature. Many global industries try to implement this technology, and there are loads of successful examples. Here are a few:
- An electronic passport (e-passport) contains a microchip with the same biometric information as a conventional passport. The chip contains useful information about the passport holder, including their digital image, which is connected to the owner's identifying information. This way, the passport is secure, and it checks the owner's identity through biometric information such as fingerprints.
- Biometrics are also used in healthcare. Hospitals need to accurately track patients and make sure that a patient's information is secure. The biometric data allows hospitals to store and access patient medical history easily.
Beyond these cases, we know that people use biometric authentication system to unlock their phones, access their online banking applications, or make secure transactions. These systems are widely known as FaceID or Touch ID and are used by billions of people worldwide every day.
How does biometric authentication work?
In order to understand how biometric authentication works, we should know that it is a process of verifying an identity using a person's unique characteristics. The solution itself looks pretty straightforward, but the technology behind it is complicated. Let's see how it works.
'Biometrics' is another word for your body measurements. So the system verifies you as a person based on these measurements. Biometric authentication takes this data and uses it to compare your features against a database. This is the way it enters your information into the system.
It works by comparing two different sets of data - the first one is set by you, the device owner. And the second one belongs to the visitor to this device. If these two sets of data are identical, the device assumes that the 'owner' and the 'visitor' are the same, so it lets you proceed with using the service. For example, if someone else holds your smartphone, and tries to use Face ID to unlock the device, they'll be rejected as the owner of the phone (you) and the visitor (the person holding your phone) don't match.
Types of biometric authentication
There are various ways to authenticate people using their biometric features. We can classify them into two main categories. The first can be the physiological identifiers, which includes things like face, voice, or even vein recognition. The second type would be behavioural identifiers, and it can be the unique ways that individuals act, like typing patterns for example. The most widely spread types of biometric authentication systems are physiological identifiers. Let’s take a look at a few:
- Fingerprint recognition is the most popular and most developed biometric authentication solution. There are several reasons for that - it’s easy to capture, and verification happens by comparing the unique loop patterns. There are specific algorithms that produce unique digital biometric templates for everyone, which helps machines understand who wants to access devices.
- Another widely spread biometric authentication solution is facial recognition, which measures the geometry of a face using multiple points - for example, the distance between eyes and from chin to the forehead.
- Voice recognition is also a common biometric authentication method. From the behavioural perspective, the way each person says something is unique - movement variation, pace, accent, and multiple other things form an individual voice that can have a great use to develop biometric authentication.
There are multiple more ways to authenticate someone based on their biometric features. It can be iris recognition, retinal scan, signature recognition and much more. Companies, to this day, try to develop new ways to secure their services with biometric authentication systems, which has a great impact on our digital lives.
What are the types of biometric devices?
Biometric authentication systems are improving fast and becoming more popular every day. But this process requires technological improvements as well. In the digital environment, it is becoming a standard to identify users and secure services using biometric devices.
It can include a reader or scanning device, which helps to identify physical features. There is also software that converts the scanned biometric data into a digital format, which most people experience daily while using Face ID. Additionally, it needs a database to store biometric data for comparison purposes - this is the core element of an authentication procedure.
Advantages of biometric authentication
There are many advantages of using biometric authentication methods over traditional forms of security, like the oft-used and oft-forgotten, passwords. Let’s start with the fact that biometric data is much harder for fraudsters to steal. The overall structure of biometrics guarantees the security of every individual. This is because of the unique physiological features that are registered in the database.
Security is a huge factor when it comes to resetting credentials or verifying remote employees when they need to access high-risk or sensitive company data. Knowing that biometric authentication can make these services much more efficient and secure to use, there is definitely a huge potential in this kind of technology.
At the same time, it is much easier to use applications with biometric authentication systems because, unlike passwords, there is nothing to remember, and it’s more comfortable to access various services this way.
Here at Veriff, we work hard to build trust online and make the digital world safer with the tools we are building daily. That’s why we recently introduced Face Match - the AI-powered reverification tool which utilizes some of the best parts of our existing identity verification technology.


