What is two-factor authentication? (2FA)
The vast majority of two-factor authentication methods rely on a knowledge-based factor followed by a possession-based factor or a biometric factor. However, on occasion, systems that require even greater levels of security may combine more than two of these different factors in order to create a multi-factor authentication (MFA) process.
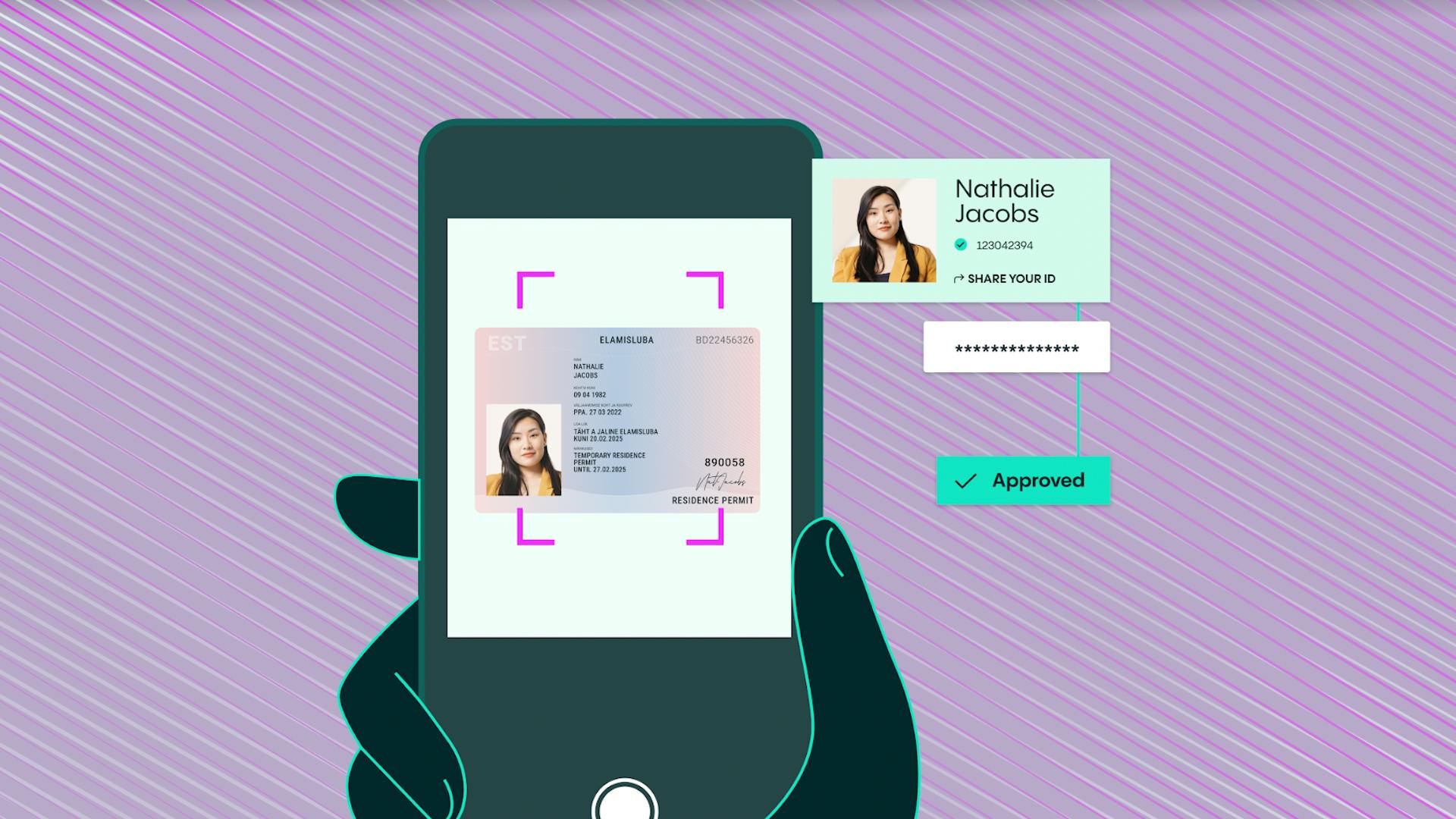
Two-factor authentication, also known as 2FA, is a security process that strengthens access security. It does this by asking a user to provide two different authentication factors in order to verify their identity. For example, as well as providing their username and password, a customer may also be asked to provide a selfie or a one-time PIN that’s sent to their smartphone.
Businesses employ this authentication method because it provides a much higher level of security when compared with single-factor authentication (SFA), in which the user only provides one piece of identifying information, such as a password. This is because, even if a user’s password becomes compromised and falls into the hand of a fraudster, this criminal actor still cannot access the customer’s account because they do not have the second authentication factor. This is usually either a security token or a biometric factor, such as a fingerprint or facial scan.
Factors of authentication
Before we discuss how two-factor authentication works in practice, we first need to understand the various factors of authentication available.
At present, most authentication methods primarily rely on knowledge-based factors. Examples of this type of authentication factor include traditional passwords.
However, two-factor authentication processes involve more than one type of authentication factor. Other factors of authentication include:
- A possession factor: This is something a user has, such as a token, a mobile device, or a smartphone app. These can be used to approve an authentication request
- A biometric factor (also known as an inherence factor): This is something that is inherent to the user’s physical self. The user may be asked to authenticate their fingerprint in a reader, submit a selfie, or provide a voice sample
The vast majority of two-factor authentication methods rely on a knowledge-based factor followed by a possession-based factor or a biometric factor. However, on occasion, systems that require even greater levels of security may combine more than two of these different factors in order to create a multi-factor authentication (MFA) process.
How does two-factor authentication work?
As you may have guessed, the way two-factor authentication is enabled depends on the vendor and the factors of authentication involved. However, that said, the majority of two-factor authentication processes broadly follow this multi-step process:
- The user is prompted to log into their account
- The user then enters their username and password. At this point, the website’s server will find a match for this information in the database
- The website will then prompt the user to initiate the second login step. At this point, the user will be asked to provide a possession factor (such as completing login on their smartphone) or a biometric factor (like a face scan)
- After providing both factors, the user is authenticated and granted access to their account
The user must pass both parts of the authentication process in order to be provided access to their account. Depending on the security system in place, users are usually time limited during this process. They must also usually complete it within a certain number of attempts. If they do not, the user is locked out of their account.
Benefits of two-factor authentication
In all, two-factor authentication provides both businesses and customers alike with a number of benefits.
The largest benefit experienced by 2FA is the increase in security that the solution provides. This is because it greatly decreases the chance a hacker can gain access to a customer’s account or any sensitive information that a business holds. Overall, 2FA can help a business address the following threats:
- Stolen passwords
- Phishing attempts
- Social engineering
- Brute force attacks
- Key logging
On top of this, two-factor authentication also provides the following benefits:
- Lowers help desk and security management costs: 2FA provides a safe way for users to reset their own passwords. This means that businesses can reduce the number of time-consuming password resets their help desk must carry out. Ultimately, this also leads to increased productivity
- Reduces operating costs: Notifying customers that you’ve witnessed suspicious activity on their accounts costs you time and money. 2FA reduces the occurrence of fraud and means your staff members don’t need to spend their time helping your customers secure their accounts. While there may be upfront costs in implementing 2FA, the investment more than pays for itself in the long run
- Increased employee flexibility: By securing internal systems with 2FA, you can allow more members of staff to work flexibily. After all, 2FA implementation allows employees to safely access corporate systems from any device or location without putting sensitive data at risk
- Increased customer trust: In the modern world, hacks and data breaches are becoming increasingly common. As a result, customers like knowing that their data is secure. So, as long as you explain why you’ve put extra steps in place (which some customers may believe are annoying or unnecessary), you can build trust with your customers
Does two-factor authentication prevent hacking?
While two-factor authentication does improve security, the system is not foolproof and cannot entirely prevent hacking and account takeovers. This is because hackers and fraudsters who are able to acquire the additional authentication factors are still able to gain unauthorized access to accounts.
As part of this, some hackers have also developed advanced methods of stealing customer data. These methods include phishing attacks, malware, and fake account recovery procedures. In these instances, an unwitting customer inadvertently provides the hacker with all the information they need to take over an account, even when a 2FA system is in place.
Similarly, hackers also have the ability to intercept text messages that are used in 2FA (this is particularly simple if they’ve stolen the customer’s phone). In some instances, a hacker may even get in touch with the target and claim to be from a company that needs the customer to repeat the number to them. In doing this, the customer provides the hacker with the second piece of information they need.
However, even though there are still flaws linked to 2FA, the process is still much more secure than password protection alone, which regularly leads to hacks and data breaches.
To experience the highest possible level of security, companies should look to employ 2FA with a biometric identifier, which makes hacking incredibly difficult. After all, even if the hacker steals the customer’s phone, they still do not possess their fingerprint and cannot bypass this security check. Alternatively, they should add additional factors to the authentication process.
Two-factor authentication use cases
By using 2FA, businesses from all industries can stay ahead of emerging security threats. Examples of how different businesses are using 2FA include:
Banking
Online banking has made it much easier for customers to manage their finances. However, remote banking has also provided hackers with a chance to target the account of a user and drain their funds.
2FA is an effective way of keeping customers and their accounts secure. Firstly, the customer is asked for their basic online banking information, such as their username and password. Then, if the customer is using the bank’s mobile app, they’re usually asked to provide a fingerprint or a face scan before they’re given access to their account. If the customer is banking online, then a one-time passcode will usually be sent to their phone. The customer will then only have a couple of minutes to enter this code before they’re timed out of the session.
Social networking
Nowadays, almost every social networking site (including Instagram, Facebook, Twitter, and TikTok) allows users to secure their accounts with two-factor authentication.
This is a particularly important step, as social networking sites are a primary target for fraudsters who wish to access vast swathes of customer information. As users primarily engage with social media sites in order to reconnect with friends and family members, many users are simply unaware of the information they provide the site. This includes crucial identifying factors, such as their:
- Full name
- Email address
- Phone number
- Address
- Date of birth
Plus, in posts, users also reveal information that a fraudster can use to help them guess a user’s security questions, such as the name of their pet and their mother’s maiden name.
Due to this, users must secure their accounts with two-factor authentication and take precautionary steps to ensure their posts can only be seen by their friends and family members.
Crypto
Crypto-related crimes take many different forms, including phishing scams and malware attacks. By embracing 2FA, crypto companies can help users secure their accounts and keep their crypto safe.
In the crypto space, 2FA authentication options take the form of desktop or mobile software apps, specialized hardware, or SMS messages.
How to set up two-factor authentication for businesses
In order to set up multi-factor authentication, businesses employ the help of a third-party provider like us.
With the help of an identity verification solution, you can take a step beyond passwords and ensure that only honest customers can access your services. Our biometric authentication solution is identity-focused rather than device-focused, meaning that it provides you with a more robust level of security and helps you bypass some of the pitfalls associated with knowledge-based and possession-based authentication.
It works by asking the user for a quick selfie. The selfie is then compared to a previously verified face and identity and checked for liveness and realness. All this means it’s simple for users to avoid account takeovers, reset their login credentials, and conduct high-value transactions securely.
Speak with the authentication experts at Veriff
If you’d like to discover more about user authentication, then contact our experts today. Simply provide us with a few basic details and we’ll create a personalized demo that shows you exactly how our solutions can help fulfill your needs.


