Fraud Article
Adversary-in-the-Middle fraud: A growing concern for businesses in 2025
Fraud is evolving at lightning speed, and businesses are constantly under constant threat. Impersonation attacks still reign supreme, but a new danger is on the rise—adversary-in-the-middle (AiTM) attacks. According to the Veriff Identity Fraud Report 2025, these sophisticated cyber threats have surged by 46% in just one year, targeting industries like iGaming and financial services. As fraud becomes more complex, staying ahead of these tactics is more critical than ever.
What is Adversary-in-the-Middle (AiTM) fraud?
Adversary-in-the-Middle (AiTM) attacks represent a significant security threat, allowing malicious actors to intercept and manipulate communications to steal data or gain unauthorized access. Techniques such as ARP poisoning, email hijacking, Wi-Fi eavesdropping, session hijacking, IP spoofing, and DNS spoofing are commonly employed in these attacks.
DNS spoofing, or DNS cache poisoning, is a particularly dangerous method where attackers inject corrupt DNS data into a resolver’s cache. This causes users to be redirected to malicious websites without their knowledge, compromising sensitive information. Unlike standard AiTM techniques that focus on intercepting and relaying communications, DNS spoofing targets the address resolution process itself. By altering core DNS infrastructure, attackers can redirect traffic from multiple users to fraudulent destinations simultaneously. This ability to disrupt large-scale internet navigation makes DNS spoofing a highly effective and far-reaching attack vector.
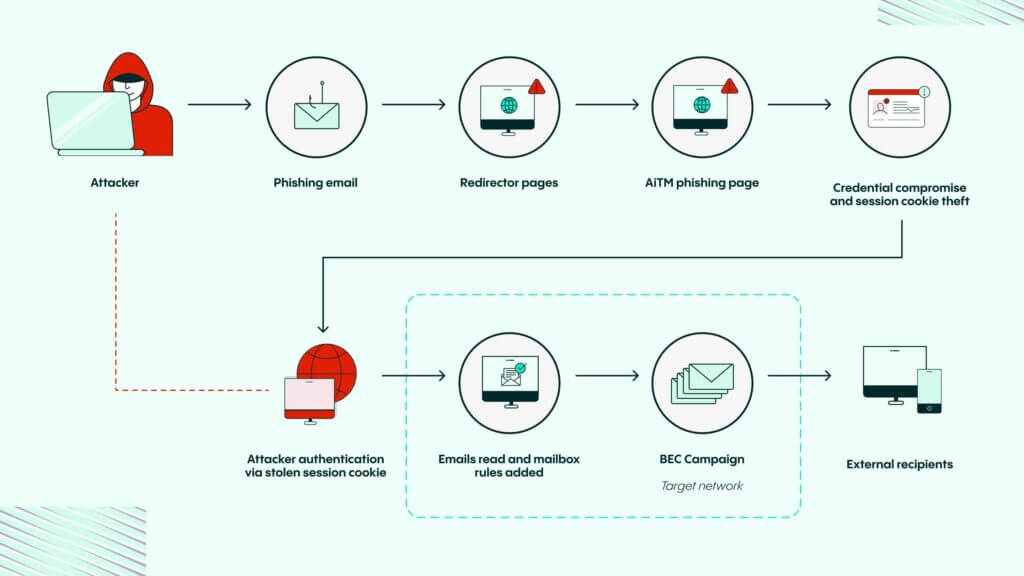
Similarly, AiTM (Adversary-in-the-Middle) attacks also target user trust, but take a different approach. These attacks intercept communication between a user and a legitimate service through phishing techniques. In an AiTM attack, the attacker typically sends a phishing email containing a link that directs the victim to a fake login page (redirector or AiTM phishing page) designed to mimic a legitimate service. When the victim enters their credentials, the attacker captures these details and may also steal session cookies to bypass multifactor authentication (MFA). Using stolen session cookies, the attacker can authenticate themselves into the victim’s account, gaining unauthorized access to emails or other resources. This access is often exploited for malicious campaigns, such as reading sensitive emails, altering mailbox rules, or initiating Business Email Compromise (BEC) schemes to target external recipients in the victim’s network.
As fraud detection and prevention technologies become more advanced, attackers are adapting their tactics to exploit the weakest point in the security chain: the identity holder. Instead of directly targeting secure systems, fraudsters increasingly use sophisticated techniques like adversary-in-the-middle (AiTM) attacks to manipulate legitimate users into unwittingly facilitating malicious activities. Attackers can intercept data if a user authenticates into an application using an unsecured protocol like HTTP.
Ira Bondar, Fraud Platform Lead at Veriff, highlights the alarming rise in these attacks, stating, “The rise in adversary-in-the-middle attacks is a very worrying trend. My thought here is that the security which protects identity verification and accounts from third-party abuse has become so good that the fraudsters are now looking towards the next weakest link in the chain, which is often the genuine identity holder, to perform the malicious act. Fortunately, Veriff is just as well equipped to fight these increasingly common adversary-in-the-middle attacks as we are with impersonation fraud.”
By leveraging its advanced technology and expertise, Veriff ensures that both systems and users are protected against this emerging threat. This dual-layered approach is critical in an era where attackers constantly evolve their methods to outpace traditional fraud prevention measures.

The rise in adversary-in-the-middle attacks is a very worrying trend. My thought here is that the security which protects identity verification and accounts from third-party abuse has become so good that the fraudsters are now looking towards the next weakest link in the chain, which is often the genuine identity holder, to perform the malicious act. Fortunately, Veriff is just as well equipped to fight these increasingly common adversary-in-the-middle attacks as we are with impersonation fraud.
Physical AiTM fraud on the rise
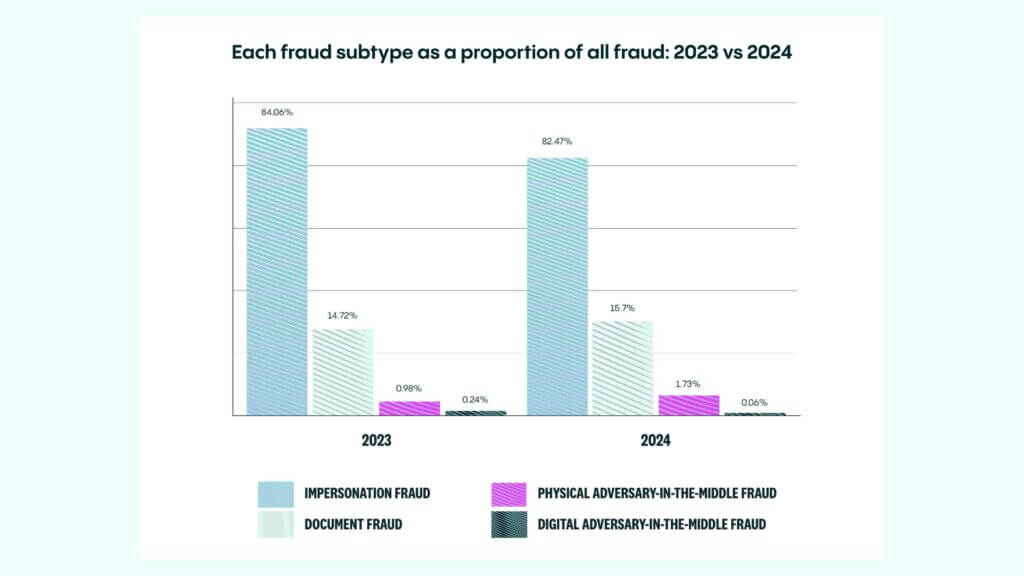
According to Veriff Identity Report, 2025, physical AiTM fraud has notably increased, from 0.98% in 2023 to 1.73% in 2024. Unsurprisingly, the iGaming sector experienced a significant surge during this period, driven by opportunities such as sign-up bonuses and rewards. Fraudsters leverage tactics like:
- Multi-accounting: Creating multiple accounts to exploit promotional offers.
- Identity farming: Using stolen or fabricated identities for fraudulent activities.
- Account takeovers: Gaining access to legitimate user accounts, often through coercion or collaboration with account holders.
In some cases, individuals are forced to grant access to their accounts or willingly participate in fraud schemes, further complicating detection and prevention efforts.
Digital AiTM fraud: A rare but growing threat
Digital AiTM fraud, while relatively rare (0.06% in 2024), is gaining traction due to advances in phishing techniques and AI-driven attacks. These schemes typically involve:
- Phishing emails: Crafted to trick users into sharing login credentials.
- AI-generated messages: Mimicking legitimate communication to deceive users.
- Malware: Intercepting communications between users and businesses to steal sensitive data or access accounts.
The goal of these attacks is often to exploit the trust between users and organizations, bypassing traditional security measures.

Identity Fraud Report 2025
Get the Identity Fraud Report 2025 and discover global data on consumer attitudes to fraud, risk, and digital identity.
Regional characteristics: US & UK perspectives on AiTM fraud
US context:
In the US, adversary-in-the-middle (AiTM) fraud increasingly targets high-value industries like financial services and e-commerce. The widespread adoption of online banking and digital payments has created a fertile ground for sophisticated phishing schemes and AI-driven attacks. Additionally, the lack of universal privacy regulations compared to the UK (e.g., GDPR) presents varied security landscapes across states, making it challenging for businesses to implement consistent defenses. Phishing-resistant MFA, robust behavior monitoring, and AI-driven fraud detection systems are critical for protecting US organizations, where the financial impact of fraud tends to be higher due to the scale of operations.
UK context:
In the UK, AiTM fraud has seen a rise, particularly in sectors like iGaming and fintech, where compliance with strict regulations such as the FCA and PSD2 is mandatory. Fraudsters often exploit promotional offers and rewards in the iGaming sector, leveraging identity farming and multi-accounting. The UK’s emphasis on strong customer authentication under PSD2 provides a framework for combating such threats, but businesses must also adopt advanced measures like biometric authentication and end-to-end encryption to ensure compliance and security. Awareness campaigns and customer education remain vital, as the UK population heavily relies on digital channels for financial transactions.
By addressing these region-specific characteristics, businesses can better tailor their strategies to counter AiTM fraud and safeguard their operations.
AiTM threats across Veriff´s key industries
Adversary-in-the-Middle (AiTM) attacks represent a sophisticated cybersecurity threat, impacting industries that rely on secure digital transactions and data privacy. These attacks are increasingly evident in sectors Veriff supports, including financial services, marketplaces, mobility/transportation, and online gaming, where the consequences can be severe—ranging from financial losses to compromised user trust.
Financial services fraud
AiTM attacks pose a significant risk to online banking and financial institutions. Cybercriminals intercept transactions, alter payment details, and redirect funds to fraudulent accounts, leading to massive financial losses. For businesses, this results in customer trust erosion and regulatory scrutiny.
E-commerce & marketplace manipulation
In marketplaces and gig platforms, AiTM attackers exploit vulnerabilities to intercept and modify transactions through data manipulation, redirecting payments to their accounts. This manipulation not only causes monetary losses, but also damages the reputation of platforms unable to secure their payment systems. In mobility/transportation sectors and beyond, AiTM techniques are often used to steal sensitive communications, intellectual property, or operational data. The extracted information may be used for industrial espionage or sold on the dark web, resulting in competitive disadvantages and privacy violations.
Mobility & transportation AiTM attacks
In the mobility and transportation sector, Adversary-in-the-Middle (AiTM) attacks pose a significant threat by intercepting communications between service providers and users. Attackers may manipulate payment systems, rerouting funds from ride-hailing apps, public transport systems, or vehicle rental services to their accounts. Additionally, these attacks can target vehicle telematics systems, intercept or alter data to compromise operational safety, track vehicle locations, or disrupt logistics operations. For transportation companies, this results in financial losses and jeopardizes customer trust and safety. Robust security measures are essential to safeguard sensitive data and maintain operational integrity in this increasingly digitized sector.
Gaming account takeovers
Online gaming platforms are prime targets for AiTM attackers for account takeover fraud, who compromise user accounts to exploit in-game purchases, rewards, or assets. These attacks undermine player trust and may lead to significant revenue losses for gaming companies.
How businesses can protect against AiTM fraud
Adversary-in-the-middle (AiTM) attacks are stealthy and often undetectable by the targeted user, making preventive measures critical. Both users and application developers share responsibility for minimizing the risk of these attacks. Below are key strategies for safeguarding against AiTM attacks:
Enable Two-Factor Authentication (2FA)
Use 2FA on email accounts to prevent attackers from successfully authenticating, even if they obtain your credentials. The additional authentication layer, like a PIN, remains inaccessible to the attacker.
Monitor network traffic
Utilize traffic analytical tools to identify suspicious activity. These tools provide insights into port and protocol usage across devices, helping administrators detect potential threats.
Implement certificate pinning
Developers can use certificate pinning in mobile apps to whitelist trusted certificates, blocking attacker-controlled ones. This proactive measure protects the application against tampered communications.
Use a VPN on public Wi-Fi
Virtual Private Networks (VPNs) encrypt data, ensuring that intercepted information remains unreadable. VPNs also protect against weaker encryption protocols by employing their own algorithms.
Phishing awareness training
Educate employees to recognize phishing attempts, which are often precursors to AiTM attacks. Preventing employees from clicking malicious links or sharing credentials reduces the risk of malware installation.
Enhance email security
Employ email filters to quarantine phishing attempts and malicious attachments. This additional layer of protection helps administrators manage potential threats effectively.
Avoid unverified Wi-Fi hotspots
Always verify the legitimacy of public Wi-Fi networks. Malicious hotspots are often designed to mimic official sources and can expose users to interception risks.
By adopting these practices, individuals and organizations can significantly reduce their vulnerability to AiTM attacks, ensuring a safer digital environment.
How can Veriff help?
Veriff is uniquely equipped to combat adversary-in-the-middle (AiTM) attacks by providing robust identity verification solutions that safeguard both users and systems.
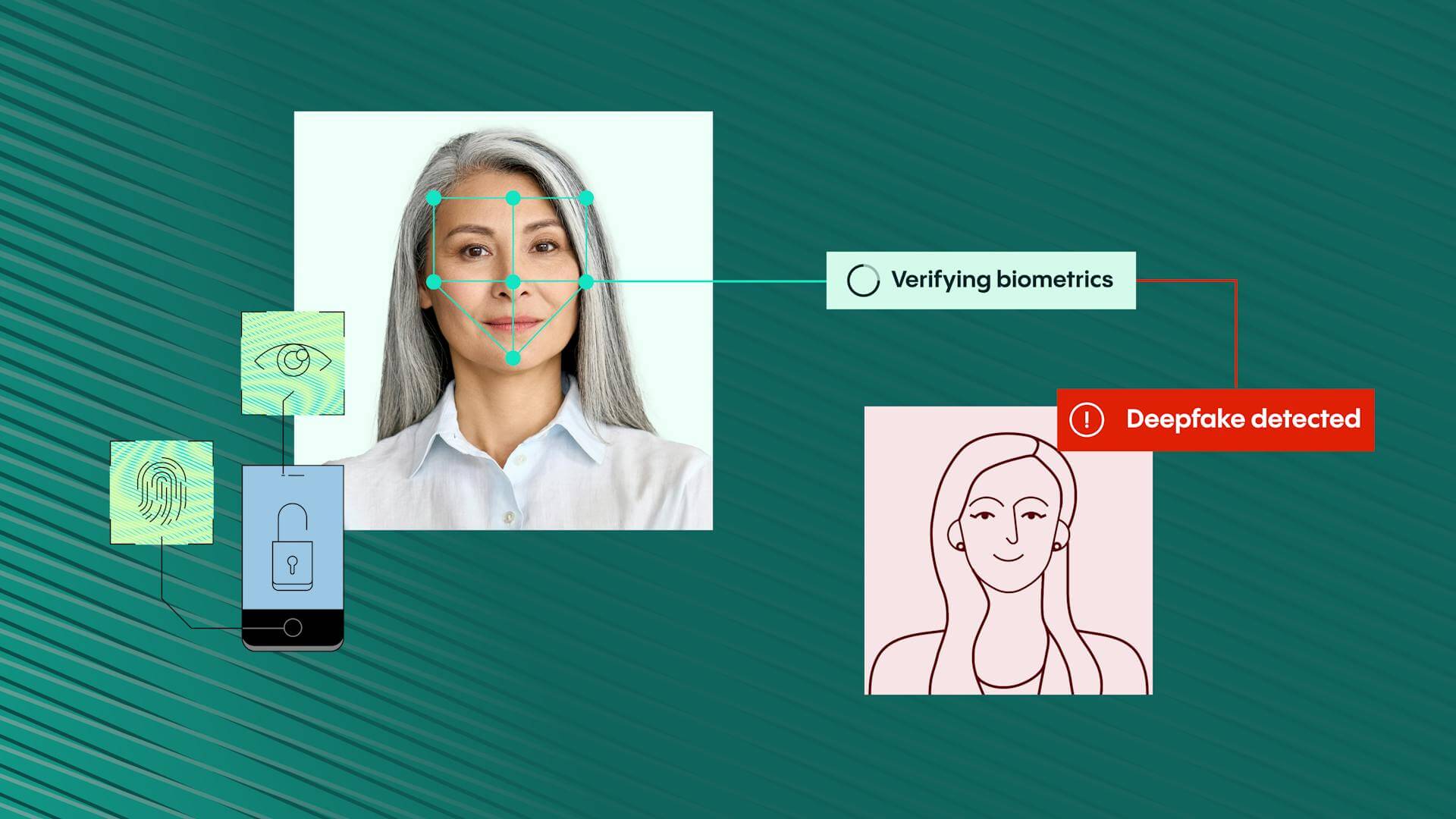
Through advanced biometric authentication and dynamic fraud detection algorithms, Veriff ensures that even if attackers intercept data or credentials, they cannot impersonate a legitimate user. Veriff’s real-time monitoring capabilities and machine learning models identify unusual behaviors indicative of AiTM tactics, such as rapid session switching or irregular device activity. Additionally, Veriff empowers organizations to implement stronger verification workflows, like multi-factor authentication (MFA) integration, to add extra layers of security. By continuously innovating and adapting its technology to address emerging threats, Veriff provides businesses and individuals with the tools necessary to stay one step ahead of fraudsters, ensuring trust and security in every interaction.
Conclusion: Staying ahead of AiTM threats
As fraud continues to evolve, adversary-in-the-middle (AiTM) attacks are becoming a significant concern, particularly for industries like financial services, fintech, and iGaming. With a 46% increase in AiTM cases in just a year, these sophisticated threats exploit vulnerabilities in both digital and physical systems, posing challenges that traditional fraud detection measures struggle to address. While impersonation fraud remains the most prevalent type of attack, the rapid growth of AiTM fraud underscores the need for organizations to adapt their defenses.
To effectively combat this emerging threat, businesses must adopt a multi-layered approach, integrating advanced security technologies, rigorous user education, and compliance with region-specific regulations. Veriff’s cutting-edge identity verification solutions, including biometric authentication and machine learning-driven fraud detection, offer a proactive defense against AiTM tactics, ensuring that both users and organizations are protected. By staying ahead of the evolving fraud landscape, companies can safeguard their operations, maintain customer trust, and build resilience against future threats.